I’ve previously covered getting your HackRF set up in Linux and getting the firmware updated. In that guide we installed the very easy to use CubicSDR application and were able to easily tune to various audio signals.
Today we’re going to do something more interactive and actually use the transmitter. We’re going to unlock and lock my vehicle using the HackRF! Let’s get started.
Hardware Used

The HackRF is a software defined radio (SDR) receiver and transmitter with a range of 1MHz all the way to 6GHz. With the use of software like CubicSDR, SDR# or GNU Radio you can decode and listen to / view almost any signal (including the International Space Station)!
Links: Amazon.com*, AliExpress.com*, Amazon.com.au*, Amazon.co.jp*, Amazon.co.uk*, Amazon.de*, Amazon.es*, Amazon.fr*, Amazon.it*, Amazon.nl*, Amazon.pl*, Amazon.se*, Amazon.sg*

The RaTLSnake M6 v2 kit comes with 3 different types of antennas that all excel at receiving different signals. It includes a telescopic antenna (like you’d see on a car) and more interestingly a helical (meant for roughly 700-1200MHz and has the 3 blue rings) and DVB-T2 (meant for 1100-1800MHz) antenna! This kit will allow you to decode quality signals in all the common frequencies used!
Links: Amazon.com*, Amazon.ca*, Amazon.com.au*, Amazon.co.jp*, Amazon.co.uk*, Amazon.de*, Amazon.es*, Amazon.fr*, Amazon.it*, Amazon.nl*, Amazon.pl*, Amazon.se*, Amazon.sg*
Locating FCC ID
The first place to start is by actually looking at your keychain/FOB. This will have a FCC ID that will give us all the information we need to capture and replay the lock/unlock codes.
Here is what mine looks like for the 2006 Chrysler 300C we previously connected to in my ODBII wireless car diagnostic tool article:

It’s very hard to read in the picture. If your key is very worn like mine the trick is to rotate it in the light. You will be able to read it when the light hits the etched text even when it’s worn like this.
On mine the FCC ID was: KOBDT04A
We can then take that ID and put it at the end of the fccid.io URL like this:
https://fccid.io/KOBDT04A
This will take you to a list that can help you find the frequency information we are looking for. Mine looked like this:
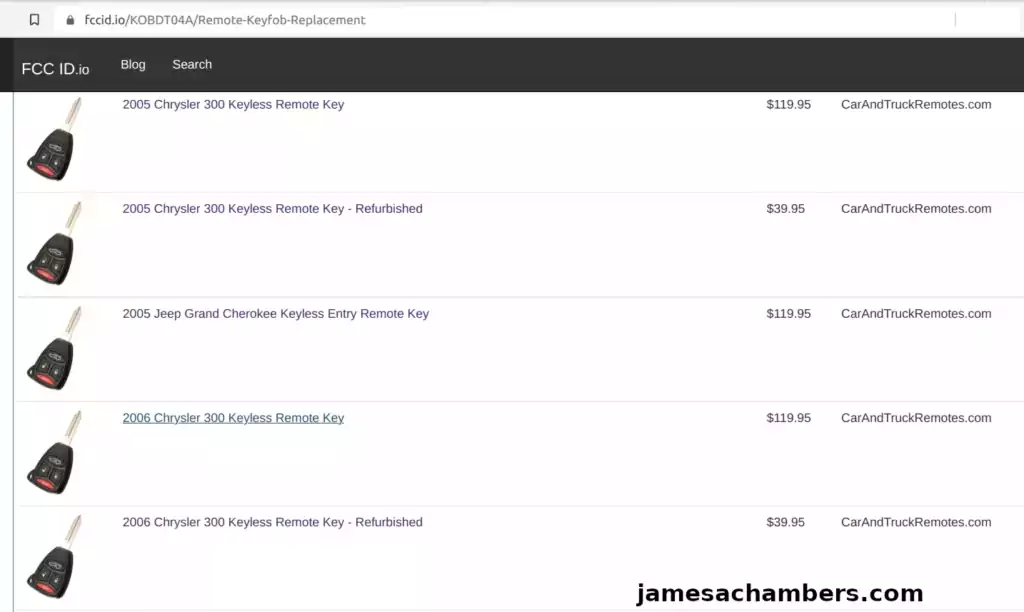
I selected the page for my key and it took me to a product site that had the information I was looking for. This will vary by product sites (try several if you’re having a hard time finding it).
Here’s an example:
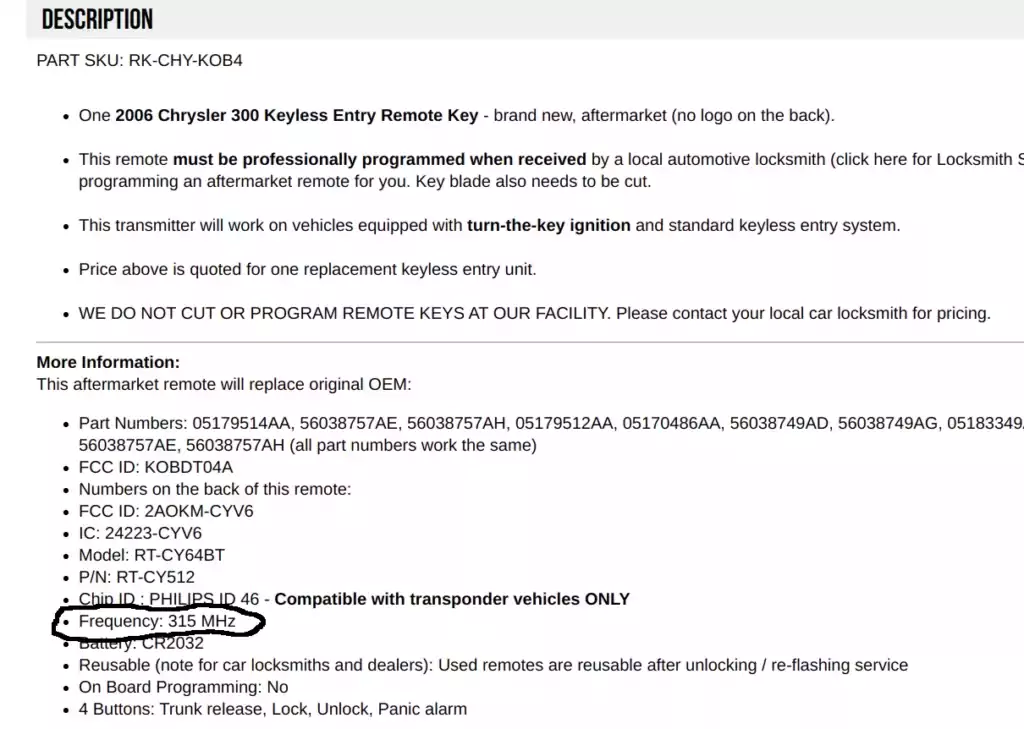
The frequency I’m looking for with this device is 315 MHz.
Monitoring Frequency
Now that we’ve located the frequency we need to be looking for we can begin using the HackRF to find the lock / unlock codes for the vehicle.
I will use CubicSDR to monitor and intercept these transmissions from my key. I have covered in a previous guide how to set up the HackRF and get CubicSDR so follow that first if you need to and you will have this application.
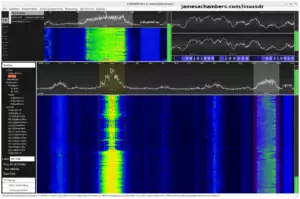
I tuned CubicSDR to 315,000,000 or 315 MHz. It was completely silent like this:
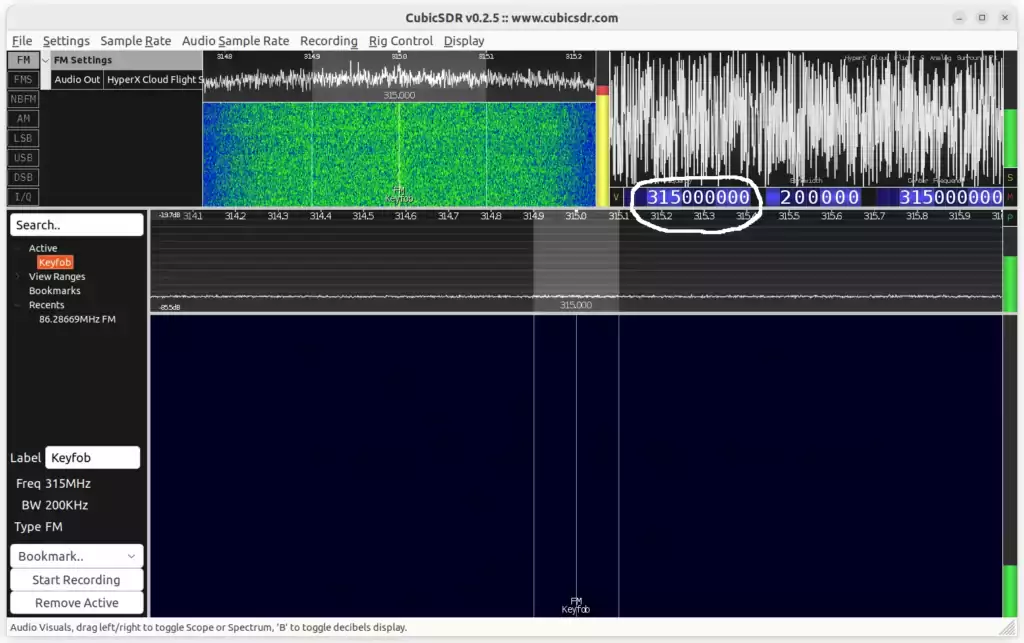
Notice there’s really nothing to see here. Watch what happens though when I start pressing “Lock” or “Unlock”:
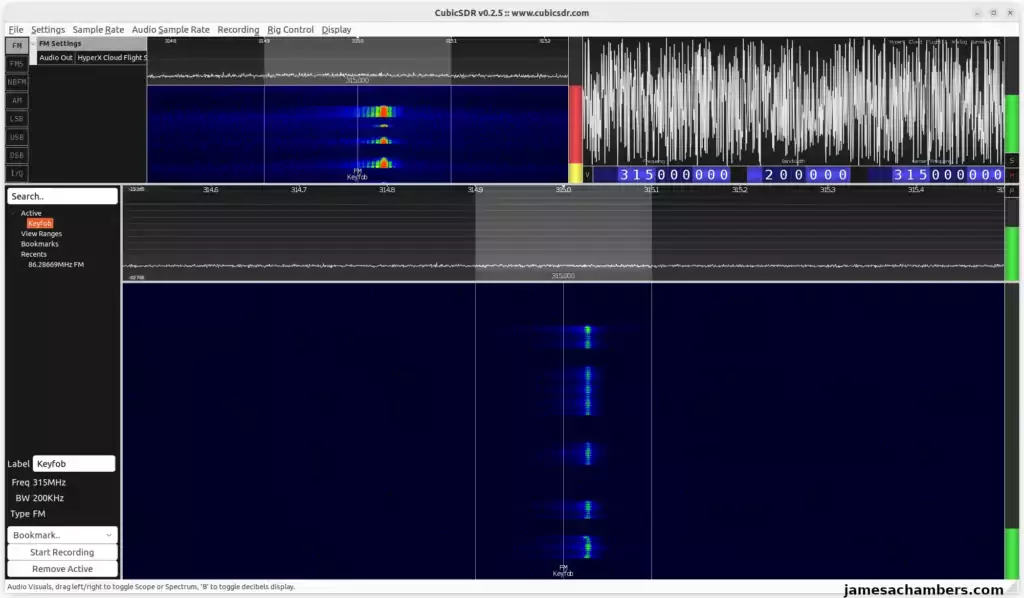
It is interesting to listen to the signal as well. This surprised me at first as I had my headphones on but you can actually hear this signal!
Here is a YouTube video of the sound it makes:
HackRF Simple Replay Attack
The HackRF has a really neat way to do replay attacks using the built-in utilities we installed during my HackRF Getting Started Guide. We can use the hackrf_transfer tool for this purpose.
Here is an example of how to perform a capture. You should put your frequency in the -f parameter (mine was 315 MHz which would be 315000000). Let’s save the file to the name “unlock”:
sudo hackrf_transfer -s 2000000 -f 315000000 -r unlock
The way you perform the capture is run this command and press the “Unlock” button. Now hit Ctrl+C to stop the capture in your command prompt window. This will leave you with a new file called “unlock”. This is our captured unlock command!
Let’s test it now. Make sure your vehicle is locked first. The way to replay our captured file from earlier is like this:
sudo hackrf_transfer -s 2000000 -f 315000000 -t unlock -a 1 -x 24
On my system it looked like this:
$ sudo hackrf_transfer -s 2000000 -f 315000000 -t unlock -a 1 -x 24 call hackrf_set_sample_rate(2000000 Hz/2.000 MHz) call hackrf_set_hw_sync_mode(0) call hackrf_set_freq(315000000 Hz/315.000 MHz) call hackrf_set_amp_enable(1) Stop with Ctrl-C 3.9 MiB / 1.000 sec = 3.9 MiB/second, amplitude -inf dBfs 3.9 MiB / 1.000 sec = 3.9 MiB/second, amplitude -inf dBfs 3.9 MiB / 1.000 sec = 3.9 MiB/second, amplitude -inf dBfs 3.4 MiB / 1.000 sec = 3.4 MiB/second, amplitude -inf dBfs Exiting... hackrf_is_streaming() result: streaming terminated (-1004) Total time: 4.00037 s hackrf_stop_tx() done hackrf_close() done hackrf_exit() done fclose() done exit
With any luck your car will immediately unlock (if the HackRF is close enough). I originally performed this replay from my desktop but it wasn’t close enough. I ended up using a laptop and then I was able to unlock it without trouble.
Now you can capture the other commands and simply change the -r parameter from “unlock” to “lock” as an example. You could also capture the panic button, opening the trunk and any other available actions. You’d end up with a bunch of files and you would replay that file based on which action you want to perform.
Many newer cars have much more complicated entry systems that use “rolling codes”. It’s honestly similar to something like a two-factor authentication (2FA) code where you can’t use the same code every time. There are often programs (or techniques/tricks) out there to help you defeat these. For example recently all of Honda’s rolling keyless entry codes were defeated on vehicles of model year 2012 and newer.
Just keep in mind that if you have a newer vehicle especially it is almost certain to use modern “rolling codes” which makes the attacks more complicated (but not impossible). We’ll cover this more in the next section.
RollJam & Manually Bypassing Rolling Codes
There are also devices you can build specifically meant to defeat rolling codes in modern vehicles. I wanted to mention the RollJam for sure.
This is a device that contains two radios. One of them intercepts the code from the key fob essentially letting you “store” the code for later. Each time you press the button you end up getting a new “code” that you can use to execute commands on the vehicle normally (once per code). This works because the codes on many of the vehicles never expire.
If you are more interested specifically in unlocking modern vehicles rather than replay attacks the RollJam is definitely one of the techniques you are going to want to investigate. It isn’t a specific device but it’s rather a technique of using two separate radios and is usually built yourself (similar to a Pwnagotchi). These are often made up of inexpensive devices like a Teensy. I would like to build one of these eventually here (or the modern evolution of it) and will definitely cover that when I do.
There is a lot of great work done on this specific problem. If you want a deep dive on bypassing rolling code systems there is an article (along with GitHub scripts and code) by a person identified as 0x5c4r3 here that I found excellent. They say they wrote it specifically because all of the blog posts were really outdated and for really old cars (sorry I didn’t help much with that using my ancient vehicle nor do I have a newer one). That is the article you are looking for if you feel the same way / are trying to defeat these.
Conclusion
This shows how easy it is to use the HackRF to essentially intercept a signal and save a copy of it. You can then replay that signal on the HackRF to execute replay attacks. It’s simple to capture things and repeat them. More advanced attacks are also available to circumvent replay protection and the HackRF is also widely acknowledged as one of the best software defined radios to perform those attacks with as well.
If your vehicle is too difficult to attack with a replay attack you should look around for other targets around the house. Older garage door opener systems are another system that is common to try a replay attack with using the HackRF. Any system that transmits signals as commands is a potential candidate. You may also investigate using a second radio for jamming and capture codes from your actual key fob to store for replay attacks (see RollJam and bypassing rolling codes section). The jamming radio keeps those codes from reaching the vehicle so they are never invalidated and you can use them for your own commands in the future (one time for every code you store).
Systems that rely on these types of signals are everywhere. Many of them have been there for decades and are seldom noticed or thought of at all (until they break). Think about what is in your home that uses RF or any type of wireless signal. Does it have a remote control? That could be an interesting system to inspect with the HackRF and try simple replay attacks and see what you can do.
The older the systems are the easier it will be as a rule of thumb (although it’s surprising how many brand new devices still have no protection against replay attacks). The process for a replay attack is exactly the same on any of these devices. Capture the signal and then replay it with the HackRF. It doesn’t take very long to try it on any given system either.
The garage door opening system is on my to-do list (and a few other wireless/RF systems around the house) and I’ll definitely write about it on the blog if they yield any interesting results. My garage door system is only a couple of years old so it will be interesting to see what kind of replay protection it has on it.
This is a very simple but very powerful method that works well with things that have simple commands like “Open”, “Close” or “Lock”. It was also interesting to actually hear the signal over my headphones!
Other Resources
I cannot recommend 0x5c4r3’s article enough if you are trying to find information about rolling codes on newer vehicles/devices
For the best upgrade you can do with your HackRF see my Upgrading HackRF One to PortaPack H2 guide!
My original HackRF Software Defined Radio Guide for Linux will give you all the utilities I used in this article to perform the replay attack
Speaking of interfacing with your vehicle also see my Read and Reset Car Codes – Wireless ODBII Diagnostic Tool guide
The Pwnagotchi tool is an interesting tool made with a Raspberry Pi Zero that automatically grabs handshakes from WiFi networks (and can even crack them)


Hi sir i need to buy hack RF z relay attack car device how much cost of it pls reply me
Hi James thanks for this. this has been really healpful to me . I’m currently writing my college project on this. can you tell me about any sources i can cite.
Hey Avjyot,
Welcome! So this is a bit trickier of a question to answer than I thought it would be. The main reason is that some of the best material written on this is written by hackers that are straight up writing it anonymously and won’t even give their real name.
I linked to a lot of these in the article but I’d imagine that for citing in a college paper having anonymous sources that won’t identify themselves might be a sticking point unless you have some very visionary professors that would accept citations from someone using a pseudonym basically. Most professors (at least when I was in college) definitely wouldn’t have accepted this but I graduated in 2010 so it has been a while. They would have said that it has no credibility if someone won’t even put their real name on the work (even if this was a popular and well-recognized hacker pseudonym with existing published work).
This one from RTL-SDL would probably be a good source. That’s at least a real company and publication outlet that would be appropriate to cite. They also link to a bunch of other sources in the article including GitHub with projects and code. I think this is probably the type of sourcing you’d want to use for what you’re saying. Linking to projects / GitHub / code is absolutely a high quality citation in contrast to citing anonymous hacker articles online for sure.
Hopefully that helps!