The world is full of devices communicating with Bluetooth even if (or maybe especially if) you don’t realize it. Most “smart” devices are advertising some Bluetooth services (some of them even publicly writable without a password!). Even my treadmill is advertising writeable Bluetooth endpoints!
The Ubertooth One is a bluetooth and bluetooth low-energy (BTLE) capture device intended for developers and security researchers/auditors. It has an external antenna and is able to communicate at much further distances than most BTLE devices by both transmitting more powerfully and having a more sensitive antenna to listen to the response. To find out what is nearby and happening over the air this is the device you want to have.
In this guide I’ll show you how to get the latest Ubertooth tools on Kali Linux as well as update the firmware for the Ubertooth device and actually use the device!
Note that Kali is not required as I also ran these same instructions using Ubuntu 22.04 and did nothing differently. If it’s an apt-based distribution you should be fine.
Hardware Used

The Ubertooth One is a bluetooth and bluetooth low-energy (BTLE) capture device intended for developers and security researchers/auditors. It has an external antenna and is able to communicate at much further distances than most BTLE devices by both transmitting more powerfully and having a more sensitive antenna to listen to the response. Has additional features/capabilities (upgradeable through firmware) that a normal Bluetooth adapter cannot do.
Links: AliExpress*, Amazon.com*, Amazon.ca*, Amazon.com.au*, Amazon.co.jp*, Amazon.co.uk*, Amazon.de*, Amazon.es*, Amazon.fr*, Amazon.it*, Amazon.nl*, Amazon.pl*, Amazon.se*, Amazon.sg*

The Nooelec Ubertooth One enclosure gives a sturdy aluminum shield but more importantly an EMI shield to reduce interference.
Links: Amazon.com*, Amazon.ca*, Amazon.com.au*, Amazon.co.jp*, Amazon.co.uk*, Amazon.de*, Amazon.es*, Amazon.fr*, Amazon.it*, Amazon.nl*, Amazon.pl*, Amazon.se*, Amazon.sg*
Updating Ubertooth Tools
Kali Linux comes with a set of tools for Ubertooth but even the ones in the repository are outdated. The latest release at time of writing is 2020-12-R1. We can build the latest tools ourselves and this is the recommended way to keep the firmware version matched up with the tools version you have installed (the official recommendation from the developers).
Let’s start by installing some prerequisites:
sudo apt update && sudo apt install cmake libusb-1.0-0-dev git make gcc g++ libbluetooth-dev wget build-essential pkg-config python3-numpy python3-qtpy python3-distutils python3-setuptools wireshark wireshark-dev libwireshark-dev python3-protobuf python3-requests python3-numpy python3-serial python3-usb python3-dev python3-websockets librtlsdr0 libsqlite3-dev libprotobuf-dev libprotobuf-c-dev protobuf-compiler protobuf-c-compiler libsensors4-dev libwebsockets-dev libnl-3-dev libnl-genl-3-dev -y
Add root and your user account to the plugdev group (if not logged in as a root):
sudo adduser root plugdev sudo adduser $LOGNAME plugdev
Before building the utilities we need to install the libbtbb packet capture library:
wget https://github.com/greatscottgadgets/libbtbb/archive/2020-12-R1.tar.gz -O libbtbb-2020-12-R1.tar.gz tar -xf libbtbb-2020-12-R1.tar.gz cd libbtbb-2020-12-R1 mkdir build cd build cmake .. make sudo make install sudo ldconfig cd ../..
To download and install the Ubertooth tools:
wget https://github.com/greatscottgadgets/ubertooth/releases/download/2020-12-R1/ubertooth-2020-12-R1.tar.xz tar -xf ubertooth-2020-12-R1.tar.xz cd ubertooth-2020-12-R1/host mkdir build cd build cmake .. make sudo make install sudo ldconfig cd ../../..
To update the Wireshark plugins:
cd libbtbb-2020-12-R1/wireshark/plugins/btbredr mkdir build cd build cmake -DCMAKE_INSTALL_LIBDIR=/usr/lib/x86_64-linux-gnu/wireshark/libwireshark3/plugins .. make sudo make install cd ../../../../.. cd libbtbb-2020-12-R1/wireshark/plugins/btbb mkdir build cd build cmake -DCMAKE_INSTALL_LIBDIR=/usr/lib/x86_64-linux-gnu/wireshark/libwireshark3/plugins .. make sudo make install cd ../../../../..
That’s it for the tools and plugins. Let’s move on to the firmware!
Update Ubertooth Firmware
You’ll definitely want to update your Ubertooth’s firmware. My Ubertooth came with firmware from 2015 (in 2021!). It’s also highly recommended that the version of firmware on your Ubertooth matches the version of the tools you are using.
To update the Ubertooth’s onboard firmware:
cd ubertooth-2020-12-R1/ubertooth-one-firmware-bin sudo ubertooth-dfu -d bluetooth_rxtx.dfu -r cd ../..
When I ran this the first time I initially got an error like this:
┌──(root@IntelNUC)-[~/ubertooth-2020-12-R1/ubertooth-one-firmware-bin] └─# ubertooth-dfu -d bluetooth_rxtx.dfu -r libUSB Error: Input/Output Error: (-1) Switching to DFU mode… Checking firmware signature …………………………………. …………………………………. …………………………………. …….. Detached
Despite this error my update was successful. You can verify this by checking your firmware version like this:
ubertooth-util -v Firmware version: 2020-12-R1 (API:1.07)
Testing using ubertooth-spescan-ui
At this point we can run some tests and talk to the Ubertooth and make sure everything is working. Let’s pull up a visual representation of the spectrum to make sure our adapter is detecting Bluetooth activity:
ubertooth-specan-ui
It should load a new window that looks like this:
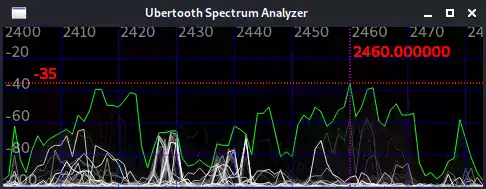
If everything is going well you should see a ton of activity like the above screenshot! Don’t worry too much about the specifics yet if that seems overwhelming. We just want to make sure you are seeing activity and that there’s not zero activity (indicating something isn’t working correctly).
Updating Kismet
Kismet has some pretty awesome tie ins with the Ubertooth and is definitely worth getting up to date. Here is a basic capture using the Ubertooth as a data source (Ubertooth placed in a window on an Intel NUC):
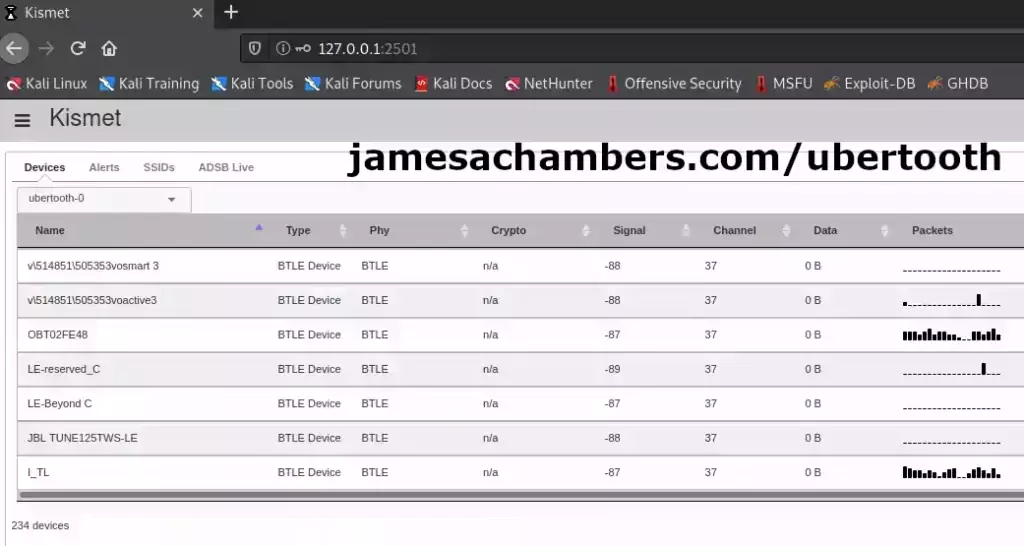
After about 30 minutes of capture the Ubertooth had seen over 234 devices! That’s unbelievable and was actually more than I was expecting to find despite undertaking this project with the suspicion that there were a lot of them out there. I’ll definitely have more to say about all of this in future articles. The last I_TL BTLE device is actually my treadmill!
The easiest way to update your Kismet is to build from source just like we did all of the Ubertooth tools and Wireshark plugins. This one will take a lot longer to compile than the other ones we have done previously since Kismet is a very large and complex application. Let’s do it:
git clone --recursive https://github.com/kismetwireless/kismet.git --depth=1 cd kismet ./configure make -j$(nproc) sudo make install sudo ldconfig sudo adduser $LOGNAME kismet sudo adduser root kismet sudo make plugins-install
That’s it. Now run Kismet and point your web browser to http://127.0.0.1:2501.
If this is your first time running Kismet here is a quick command to get the default Kismet generated login/password:
cat ~/.kismet/kismet_httpd.conf
This should reveal the login credentials to get into Kismet. If you click the gear in the top left select “Data Sources” and you should see the Ubertooth and your other devices such as your WiFi card in there. When you click a data source you should be able to enable it and it will start populating what Bluetooth activity is happening near you!
You may find references to an Ubertooth Kismet plugin but it is no longer used. The newer versions of Kismet support BTLE capture natively and the plugin no longer builds so don’t waste any time on it!
CLI Tools
ubertooth-util
This is the main utility to control the Ubertooth:
ubertooth-util - command line utility for Ubertooth Zero and Ubertooth One
Common options:
-v get firmware revision number
-V get compile info
-I identify ubertooth device by flashing all LEDs
-d[0-1] get/set all LEDs
-l[0-1] get/set USR LED
-S stop current operation
-r full reset
-U<0-7> set ubertooth device to use
-N print total number of Uberteeth and exit
Radio options:
-a[0-7] get/set power amplifier level
-c[2400-2483] get/set channel in MHz
-C[0-78] get/set channel
-q[1-225 (RSSI threshold)] start LED spectrum analyzer
-t intitiate continuous transmit test
-z set squelch level
Range test:
-e start repeater mode
-m display range test result
-n initiate range test
Miscellaneous:
-f activate flash programming (DFU) mode
-i activate In-System Programming (ISP) mode
-b get hardware board id number
-p get microcontroller Part ID
-s get microcontroller serial number
-x xmas lights
The most useful options are the -r option (reset the Ubertooth) but there are several other aspects of the Ubertooth’s behavior you may find useful in here!
ubertooth-scan
The ubertooth-scan utility scans for traditional Bluetooth devices. You can pair it with a normal Bluetooth adapter as well to do an advanced scan to find hidden devices as well:
ubertooth-scan - active(Bluez) device scan and inquiry supported by Ubertooth
This tool uses a normal Bluetooth dongle to perform Inquiry Scans and
Extended Inquiry scans of Bluetooth devices. It uses Ubertooth to
discover undiscoverable devices and can use BlueZ to scan for
discoverable devices.
Usage:
ubertooth-scan
Use Ubertooth to discover devices and perform Inquiry Scan.
ubertooth-scan -s -x Use BlueZ and Ubertooth to discover devices and perform Inquiry Scan and Extended Inquiry Scan.
Options:
-s hci Scan - use BlueZ to scan for discoverable devices
-x eXtended scan - retrieve additional information about target devices
-t scan Time (seconds) - length of time to sniff packets. [Default: 20s]
-e max_ac_errors (default: 2, range: 0-4)
-b Bluetooth device (hci0)
-U<0-7> set Ubertooth device to use
The ‘ubertooth-scan -s -x’ combo is fantastic as it performs an extended inquiry scan to discover services on the Bluetooth device. This helps us figure out what they are and what capabilities they have.
ubertooth-btle
This is the main “fun” utility for BTLE devices. It has 3 different modes (follow -f, promiscuous -p, and no follow -n). Follow mode means it will try to attempt to keep up with Bluetooth connections and capture data packets. Here’s the full overview:
ubertooth-btle - passive Bluetooth Low Energy monitoring
Usage:
-h this help
Major modes:
-f follow connections
-n don't follow, only print advertisements
-p promiscuous: sniff active connections
-a[address] get/set access address (example: -a8e89bed6)
-s<address> faux slave mode, using MAC addr (example: -s22:44:66:88:aa:cc)
-t<address> set connection following target (example: -t22:44:66:88:aa:cc/48)
-tnone unset connection following target
Interference (use with -f or -p):
-i interfere with one connection and return to idle
-I interfere continuously
Data source:
-U<0-7> set ubertooth device to use
Misc:
-r<filename> capture packets to PCAPNG file
-q<filename> capture packets to PCAP file (DLT_BLUETOOTH_LE_LL_WITH_PHDR)
-c<filename> capture packets to PCAP file (DLT_PPI + DLT_BLUETOOTH_LE_LL)
-A<index> advertising channel index (default 37)
-v[01] verify CRC mode, get status or enable/disable
-x<n> allow n access address offenses (default 32)
The interference mode help create the conditions necessary for data capture!
Conclusion
I wanted to write this because all the above information involved going to about 20 different web sites to piece together. I really would have liked to just set it all up at once like this so I figured I’d share it as well as record it for myself in the future as well!
The Ubertooth device is definitely delivering at helping me figure out what is going on over the airwaves in my own home. With hundreds of different devices sharing the airspace detectable in my home I now can investigate which ones are actually mine and secure them. Some of the devices like my treadmill have publicly writeable configuration attributes as an example. The Ubertooth lets you hunt these down and figure out what they’re doing and if anyone might be able to exploit them!
Wireless traffic of all kinds continues to get harder to detect as technology improves and time goes on. The scary part is if nefarious actors are utilizing these highly stealthy networks. Instances of IoT hacking continue to rise as these devices become more ubiquitous. This tool will help you investigate them and take control of your network airspace!
Other Resources
For the HackRF (also by Great Scott Gadgets) check out my Linux HackRF Guide or if you want to see it in action there is also my Use HackRF SDR to Lock / Unlock Car guide on replay attacks using the HackRF
You can also upgrade a HackRF to be completely portable: Upgrading HackRF One to PortaPack H2
My guide on how to build a Pwnagotchi to audit WiFi networks near you is also worth checking out!




Hello @James
Thank you for the detail instructions. However I have been having hard time to successfully run the command-line scripts in your walk through.for example when I executed first script i got the following error:
'Hit:1 http://ftp.halifax.rwth-aachen.de/kali kali-rolling InReleaseReading package lists... Done
Building dependency tree... Done
Reading state information... Done
3 packages can be upgraded. Run 'apt list --upgradable' to see them.
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
Package libsensors4-dev is not available, but is referred to by another package.
This may mean that the package is missing, has been obsoleted, or
is only available from another source
However the following packages replace it:
libsensors-dev
E: Package ‘libsensors4-dev’ has no installation candidate’
Also, I i did followed some recomended “package has no installation candidate” fixs but the problem is persistent.
Note: The system is a newly installed kali linux
thank you in advance.
Hey MB Jallow,
I think this package has been updated. It looks like it’s now just libsensors-dev. There’s a hint about this in the output:
However the following packages replace it:libsensors-dev
Can you try installing libsensors-dev instead? I’ll update the article if that works for you!
Hi James… I had the same problem that MB Jallow and it worked for me
Hey Tomas,
Thanks a ton for confirming, enjoy and take care!
Thanks James! I’ll give it shot and report back.
Thanks for getting back to me so quickly James. I ran the pip3 command that you recommended. I am now getting the following:
Eventbus got PACKETCHAIN_STATSEventbus got TIMESTAMP
Eventbus got BATTERY
Eventbus got STATISTICS
Eventbus got GPS_LOCATION
Eventbus got GPS_LOCATION
Eventbus got PACKETCHAIN_STATS
Eventbus got TIMESTAMP
This continues on a loop. I use the browser and tried to connect to Kismet (http://localhost:2501) and activate the data sources but Kismet is not able to connect. This is the newest Kali Linux download running live on a USB drive. I have had great success in the past with this setup. Thanks for any help you can provide.
Hey T Young,
It probably means the version on pip doesn’t match the version of Kismet that is in the repositories. You will likely have to build kismet-external. It says kismet-external was upgraded 3 weeks ago.
Alternatively you could not use the Kismet source at all and install. You could delete everything we’ve done and just do:
pip install kismetThen the versions will match. I think the issue though is you are trying to build kismet from source and use the repository version of kismet-external.
I legitimately have no idea what kismet-external is but I’m comfortable saying it’s a *horrible* design. Why can’t this just be a part of the kismet package? Why do we have to play dependency hell?
That is what this is. Dependency hell. Your versions don’t match each other basically.
For me to do this I would have to do a fresh install of Kali and try from scratch. It’s hard to want to do that though as I’d imagine in 2-3 weeks from now this will be fixed probably when they fix whatever is screwed up with the dependencies here right now.
Theoretically though you could just:
git clone https://github.com/kismetwireless/python-kismet-external.gitcd python-kismet-external
./setup.py
I think this will be the best way to work around it. You aren’t doing anything wrong. This is just a very badly designed application with very badly designed dependencies. They’re also constantly changing them for no reason whatsoever. Why did we need this stupid kismet-external package which is just serving to break everything?
Great design Kismet. Was this really worth breaking off an entire package for these web access endpoints when Kismet is already enormous anyways? It’s shockingly stupid. Thanks for saving us 50KB in code in the main repository and creating an absolute dependency nightmare.
I think that is all this is though. You need to get your dependencies sync’d up it looks like here. The pip version won’t be good enough and you will have to build it unfortunately. Hopefully this will fix itself before too long or I really will need to rewrite the guide (which I’m willing to do if necessary). Let’s confirm that this fixes it for you first though and then I will definitely add it to the article!
Hi James, I just finished updating Kismet but when I try to run it I am getting the following messages:
ERROR: Kismet external Python tools require the kismetexternal pythonlibrary; you can find it in the kismetexternal git or via pip
ERROR: Kismet external Python tools require the kismetexternal python
library; you can find it in the kismetexternal git or via pip
Hope you can help! Thanks and Happy New Year.
Hey T Young,
Welcome! That does seem to be a new one but you should be able to install it with:
pip3 install kismetexternalIt may also need a:
sudo pip3 install kismetexternalIt looks like maybe this is a minor dependency change or that some part of the Kismet package may have been broken off into this separate repository.
Hopefully that helps!
You helped me so, so much. I was on the “20 different web sites” until I found this blog. Thank you so much!!!
Thank you so much for the kind comment as well, you’re awesome! Take care!
thank you for the tutorial read. I was Wi-Fi hacked, been about a month now, first I thought these were hackers from far away, after some back and forth engaging, became 3 of them on my network against me just blocking the most and moving some important files, did recuperate all my email accounts except for my webhost at hostinger, they just been being dicks a few of them, hopefully my last email will fix that.
Did run a bt sniffer on the phone during a power outage and also noticed two Wi-Fi places with good signal and using another sniffer gave me the name of the bt type device not the average consumer would use. I could be wrong and it’s someone far away but they destroyed my one plus 7 pro, screen day DIE I am going to give it a try, two techs couldn’t but I already got the iPhone 11 Pro which they locked up as well up and running today. Plus all the bs can’t use my computers, even at my clinic. dentist in TJ, MX. I want to track these turds and take care of business.
They weren’t able to take any cash and I recuperated and locked with a USB key I ordered for my email accounts, except my access to my hosting was lost when they first jacked my Gmail account and stole my windows Authenticator app off my phone and everything else. Luckily I recuperated the Gmail account and locked it tight and had Gmail delete it while keeping my google business site set to a non gmail. Well that was when I had access to my site… so now accessing my google business site will take a bit since it’s on my old phone number and an email from my domain ROFL, both I have no access!
I need to get a new USA SIM of my number, already got two new numbers and another 2 local sims cards since it’s still active but they disabled or I might just port it out magicjack or an phone app. Had to buy the iphone13, holding strong so far. installing some new hardware tech for the house and office this week to keep it extra secure…
Had a CNS background before dentistry but forgot all that stuff but i think I will be fine with kali and those parts and parts…. Have a bt/Wi-Fi jammer on the way for my computer area just to be a bit safer.
And just read about kali yesterday so that my next project to do asap. Payback is going to be good….. won’t be hacking another pc with their hands at least from the accident that will happen.
Thanks, saw some small kali setups with the phone on eBay but I might buy a Linux specific refurbished laptop or pop it into my newest gaming laptop.
Who the hell did I piss off, has to be dental related, some competition… sheesh or someone in Asia from some of the names that first popped up on my Wi-Fi system in the beginning..,, Either way I will learn Kali, should be fun…
Hey Mark,
This message got sent to the spam filter but I’m not sure what it picked up about it that was suspicious other than it looks a lot like COPYPASTA and I had to read it a couple of times to be like, is this a real person? It seems real though because I don’t see why you would have wrote it because you aren’t asking for anything, you didn’t post any links, etc. so sorry for it getting caught in the filter!
So given your situation I have a few thoughts. Related to this article yes the Ubertooth could be of some use here. Will you be able to hack something like an iPhone 11 Pro with it? Not a chance in hell. Something like this is generally only possible on misconfigured devices that are unpatched / jailbroken / people purposely gave themselves dangerous permissions/rights etc.
So what is it really good for? Tracking them. Unless they have their bluetooth (and WiFi, because most WiFi uses that “bluetooth sense” feature and silently enables Bluetooth to help it find points) both shut off you’ll pick them up. The iPhone definitely emits discovery signals as you’re going around (of course, and probably not for your benefit most of the time). You can detect these and see their devices. A lot of the time there is even the device name in the discovery information that Bluetooth can see (very common to see Dude’s iPhone giving you their first name and making it pretty obvious who you are dealing with).
If you are dealing with wireless hacking it’s almost certainly WiFi. Bluetooth hacking is not easy, not many people can do it and the tools are pretty badly outdated and have a limited selection compared to most other types of hacking. WiFi hacking is *extremely* big and pretty easy relatively speaking. They could have cracked your WiFi hash in hashcat which is childs play and the only thing protecting you is using a very difficult password with a lot of numbers and symbols that isn’t really based on a dictionary word. I’ve found I can crack somewhere between 1/4 to 1/3 of random access points by grabbing the handshake and running it through rockyou.txt in hashcat and a few other big dictionaries with some decent rulesets like OneRuleToRuleThemAll.rule.
These tools are really just the beginning though. You can have the tools and Kali and not be able to do anything basically because you also need at a minimum years of background and practice to be able to use them. Documentation is spare, tools are outdated and they expect you to build them yourself often, and actually exploiting things is *VERY* hard. As in there’s honestly not a lot of people that can do it that aren’t just running prepackaged scripts of well known vulnerabilities.
That being said I wouldn’t discourage you from doing any of this. You will learn a lot about security and then you will be able to protect yourself. That is a great feeling.
The WiFi jammer may be of assistance but honestly the fact they can breach it means you need to upgrade your WiFi setup. You need a way more secure key (or WPA Enterprise even better if this is a business especially). You can’t just go into a McDonalds and hack their wireless because they are running an enterprise fleet of top tier gear that is actively managed and patched. Someone figured out though that your point is probably a few years older, maybe a few years too old, and had a password they were able to get either with a basic cracker.
Nobody can crack a point running the latest gear with a secure password though (okay, not nobody, but they are so few in number and so expensive that you will not encounter them). Upgrading the firmware to the latest and choosing a new much more complex password would probably do it. Upgrading to a modern WPA3 enterprise setup would definitely do it. I don’t think Bluetooth is the issue unless we are dealing with old Point of Sale terminals with really specific vulnerabilities.
Best of luck, make sure you don’t get yourself into trouble because some of the things you said could lead to that, especially if you don’t know how to protect yourself and cover your tracks (you don’t yet). You could still learn to take control of your own wireless better and learn to do surveillance and protect your area / property, and that would be a great thing! It also wouldn’t break any laws or turn you into what the people breaking into your devices via WiFi are.
If they are attacking your network you have the right to defend yourself and do whatever surveillance and countermeasures are necessary to maintain security (and are legal in your area/jurisdiction). Once you talk about breaking into their phones though you have become the aggressor in an attack and no longer a defender and you should understand that puts you squarely on the wrong side of the line in that encounter. If you somehow disabled the phone during an active attack on your property (and they were on your property) depending on your jurisdiction maybe. If we are talking remotely/tracking them down then that’s jail/prison time in any jurisdiction for sure.
My personal recommendation is that you upgrade your gear. You mentioned business accounts involved so you should be running a WPA Enterprise (WPA2 Enterprise at a minimum probably) network and they won’t be able to do anything to it. The normal cracking tools in Kali generally don’t work on WPA Enterprise networks because it’s not a “preshared” key with the 4 way handshake (and a bunch of other complicated technical reasons). You will have a lot more fun (and have a higher chance of success) by upgrading and just watching the idiots try to get on the monitor of a modern enterprise WiFi appliance and knowing they can’t. You don’t need to be a big company to have it, I run enterprise gear in my house. Hopefully that helps!
Hi James,
I hope you are well and I hope even more that you can help me. I am running the latest version of Kali Linux inside VirtualBox on a Windows 10 machine. I compiled/installed Kismet from source and installed all of the Ubertooth One software following the Build Guide instructions on github and updated the firmware on my Ubertooth One (1.07). The Ubertooth works using the utility, scan and btle commands. However, when I try to use the Ubertooth with Kismet (kismet -c ubertooth), I hear the sound of a USB device disconnecting and the red LED on the ubertooth turns off. There is no data being passed and an error message in Kismet. Running lsusb, I can still see the ubertooth but I can’t execute any commands. PLEASE HELP!!! I am a complete novice at this and I am at my wits end. Thanks for any assistance you can provide.
Hey T. Young,
That is strange! For sure the Ubertooth sounds like it’s crashing hard. Either that or libusb but the entire device is being dropped.
I did have this happen a few times but not too many. Sometimes it would get so stuck that the light would turn off and remain off until I unplugged the Ubertooth and then plugged it back in and the lights would come right back on and it would work. Showing in lsusb is odd. I did not check that when mine dropped and the light turned off but unplugging it and plugging it back in always got it for me but it only happened a few times during all of my testing.
My guess is that these are device/firmware level crashes on the Ubertooth. It’s strange you’re getting it every time though. I also completely built Kismet from scratch (only a month or two ago when I wrote this). Is this Kali Linux and an up to date version? What is the error message Kismet gives you?
Have you tried moving the Ubertooth to different USB ports? It may sound weird but it can matter. USB 2.0 (black ports) vs USB 3.0 ports (blue ports) can make a difference for example. Some USB hubs (both actual ones and ones that are a part of the PC and connected through various USB interfaces on your motherboard internally) are known to do this as well. Rearranging which port it is connected to (try all of them to make sure to check each internal “usb hub” on your computer) can make a difference here sometimes (especially with things like power).
Does your system have aggressive power management settings like usb autosuspend going on? Maybe it’s being put to sleep. This is an old problem within Linux on some devices / with some setups.
Does the version of your tools on Kali (if you do a -v on one of the tools) match the exact firmware version of the Ubertooth? I know you mentioned 1.07 but the output from running the software ubertooth tools inside Kali with -v should also be the same version/series otherwise we may have a version mismatch here.
Is this anything weird like a virtual machine? Mine is a real bare metal install and virtual machines are known to have some timeout issues with libusb.
Can you make sure you are added to the kismet groups?
sudo adduser kali kismetandsudo adduser root kismetshould cover it. Make sure you run kismet as sudo (as a test) with sudo kismet. Not the best security practice but definitely helps rule out things like restrictive USB permissions and other non-root related issues.Are you getting any output in dmesg or /var/log/syslog? There should be an event recorded somewhere for this since you are hearing the “sound”. I will fire up my Kali PC here though and test everything on the latest version and make sure it’s working as well!
As a followup to this I completed my initial quick validation. I did a sudo apt dist-upgrade -y on Kali Linux rolling. I also did a full rebuild of the current Kismet git source tree along with the make install:
Everything seems happy with the latest Kali / Kismet / tools shown here in the screenshot. That would definitely point toward some of my original theories from my first initial reply but I wanted to double check this as it’s not unheard of for changes in Kismet etc. to break things!
Somehow this seems environment / USB related for sure so hopefully that helps rule some things out / narrow things down. This combined with some of the ideas from my earlier reply I think should help us make some progress here!
Thanks for getting back to me James. I’m running Kali as a VirtualBox machine on a Windows 10 host computer. Here is an overview
Kismet vers: 2021-00-GITubertooth firmware: 2020-12-R1 (API 1.07)
ubertooth vers: 2020-12-R1
I ran ‘groups’ and I am in the kismet group
I have screen shots but I’m not sure how to include them in my post.
Hey T. Young,
Sorry for the slow response, it has been a busy week! I do have something for you here.
It looks like when using VMs you may need to add some filters / USB filters for the Ubertooth device to get it to work properly. Bare metal should always work but VMs can be made to work it looks like as well. It looks like these are a thing in VirtualBox as well.
I have not tried this myself yet to see if I can get it working on a VM but I will put it on the TO-DO list! It looks like the most promising route would be to get the USB device ID using the method described in the GitHub link and then set up a USB filter to immediately take control of the device when it’s plugged in. Hopefully that helps!
Hi James,
Unfortunately, none of the above seem to help. I already had the ubertooth in my USB filter list. I am getting the following message from kismet:
usb_claim_interface error -6control message unsupported
I’m still hearing the USB disconnect sound and the red LED on the ubertooth goes out. I’ll try posting in the VirtualBox forums as well. Again, thanks for all your help
It’s still libusb. It’s a very standard crash. It’s definitely because you’re virtualizing.
I’m not sure if you’ll have to rebuild the kernel with one of these flags or if blacklisting a driver will be good enough.
Reference #1
Reference #2
Reference #3
Reference #4
There’s no silver bullet to this problem that I can see. The internet is filled with libusb -6 errors. Some of these go back 15+ years and very few of them seemed to completely solve it.
I’d say these utilities don’t seem to be designed to be VM safe. If that is a requirement the Ubertooth is probably not a good choice.
I’m guessing there may be something you can do but you’re going to have to grind through -6 errors and Google and see if you can find one of these workarounds that may get it. The filter is pretty important but it could be a lot of other things like even your specific motherboards USB controller, needing to rebuild the kernel with special flags, etc.
Several of those links talk about how janky libusb is in VMs and you seem to have discovered that first hand! If you find a solution let me know but for sure this doesn’t seem like an easy fix to me. You’ll need to become a bit of a developer here to fix this!
Thank you Sir!
I hate to say it, but I’m glad this wasn’t some isolated problem that I was having. You have been a tremendous help.