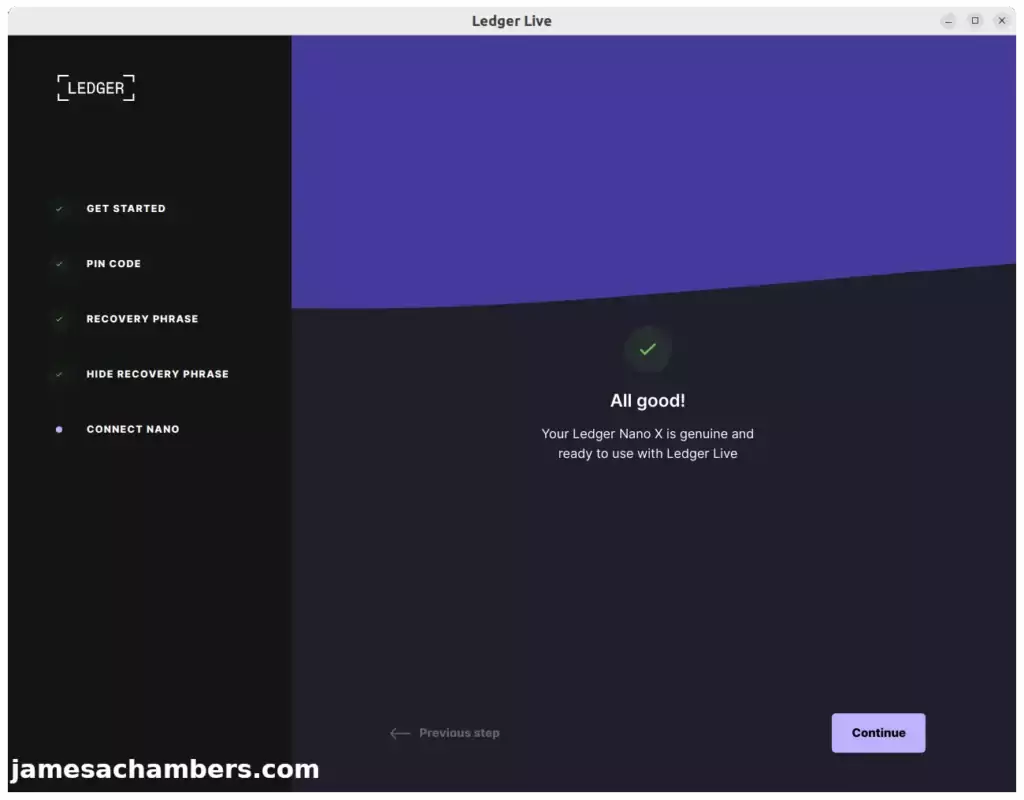
When installing Ledger Live on Ubuntu 22.04 I ran into an issue where during the genuine check it would not find my device. It was not even prompting for a PIN or showing any activity and would simply time out eventually and fail the check.
It turns out that Ledger Live needs some udev rules to work correctly. In this quick guide I’ll cover how to set up and fix Ledger Live in Linux!
Hardware Used

This version of the Ledger has Bluetooth so you are able to use it with your cell phone Ledger Live app wirelessly. Also holds a charge and has a battery!
Links: Amazon.com*
Getting Ledger Live for Linux
The official URL to get Ledger Live is:
https://download.live.ledger.com/latest/linuxThe file will be a .AppImage file. You want to set this file to executable and run it like this (assuming you saved it to your Downloads folder):
cd ~/Downloads chmod +x ledger-live-desktop-2.45.1-linux-x86_64.AppImage ./ledger-live-desktop-2.45.1-linux-x86_64.AppImage
You will very likely find that it will fail to connect to your device during the genuine check.
Fixing Udev Rules
By adding some udev rules to Linux we can fix the USB device permissions issue.
Here is the fix:
wget -q -O - https://raw.githubusercontent.com/LedgerHQ/udev-rules/master/add_udev_rules.sh | sudo bash
This is pulling from the official Ledger GitHub repository so the rules it adds are safe.
Once these are added relaunch Ledger Live and try now. You should meet with success!
Alternative Fix: Launch as sudo
You may also launch the Ledger image as sudo and pass it a special command:
sudo ./ledger-live-desktop-2.45.1-linux-x86_64.AppImage
This fix will work for some people but many of you will have GPU related errors. One way to work around it is to actually log completely out of your desktop as your regular user and actually sign in as root. It’s not fun or ideal but if the udev rule solution won’t work it’s an option.
Conclusion
I’m not sure why Ledger’s installer doesn’t take care of this. It seems to impact every Linux install unless they happen to be logged into the GUI as the “root” user already.
Nevertheless this fix got mine up and running and working perfectly!
Other Resources
You may also be interested in my Life as a “Ledger” Wallet Data Breach Victim article especially if you want to get even more upset at Ledger!






> You know how when you go to web sites to download applications for Linux and it’s almost always a .deb package and sometimes a .rpm?
Actually (and I have to restrict this to GitHub – the source of the vast majority of my packages), I find more AppImages than anything else (which obviously means that the developer intended it as a “universal” solution). And I will note that the Ledger Live wallet itself (the source of the need for udev rules under discussion) comes as an AppImage.
> If you aren’t using a source-based distribution (and I would still argue that most people aren’t…
Well, I certainly can’t disagree with that. 🙂
> …almost everything that gets distributed is going to target those more convenient distributions.
Again, AppImages (by design) should cover a much wider variety of distributions that .rpm or .deb packages do (they have to work on systems based on both of those package managers, and more).
> I was pretty close.
I will give you partial credit for that. 🙂 I definitely don’t do simple cut and paste. I can become a bit of iconoclast with my machine, wanting to change things because I don’t like the way that developers (both distribution and upstream), did them. I have no systemd, no pulseaudio (no “Lennartware” at all, for that matter), no PAM, no *.kit. Too many people want to overcomplicate everything. Look at the difference between GRUB 1 and GRUB 2, for example (glad I could ditch the latter for EFI booting).
Everything even slightly related to any technology now seems to suffer from efforts to maintain compatibility with poor choices (having the benefit of hindsight) made in the past.
> I definitely respect your passion for wanting to share this fix and I’m sure this will actually probably help hundreds if not thousands of people over time.
The Ledger customer service representative said that she passed my rules on to the development team, so if they update their script to something similar to what I wrote, I will (justifiably) take credit for it. 🙂 But even if they just stick the rules on the support page as an alternative (which could save people a significant amount of time), I would find that enough of a reward for my efforts.
Thanks for your feedback.
Hey name,
That’s great that you’ve submitted it to Ledger. Their Linux rules clearly just say “for Linux” so that implies that it should probably support a wider variety of Linux distributions. They didn’t mention any requirements as far as flavors go.
AppImages are great. I’m not sure what you are downloading though where you think these are universally available. There isn’t one for Steam. That’s kind of important. There isn’t one for TeamViewer. I do have one for KeePassXC and of course Ledger Live has one. My impression is that the companies that begrudgingly support Linux generally still don’t have these and even ones that have embraced it (like Steam) still don’t have one. All of that being said I 100% support moving toward AppImages and I’m sure we’ll see them more and more. It has to be well less than 50% of the kind of software I use that is even available in AppImage format though.
I think I gladly support everything you are doing here. They should make the rules more universal and AppImage should be more fully embraced by all companies distributing software on Linux. There is still a lot of work to be done and a lot of other companies to get on board though that do distribute widely used Linux software and basically only distribute them as debs/rpms.
I do use a lot of flatpaks on PopOS but my understanding is that Ubuntu wants to move away from flatpaks. I notice you didn’t mention flatpaks at all. That’s something people would have told me 1-2 years ago though pushing universal formats but it seems to be falling out of favor now. Is AppImage the one that is going to stick? Because Ubuntu is killing off flatpaks (at least enabled/installed by default) because they very much want to maintain the .deb world and snap packages.
My preference would actually be AppImage but this war is far from over. It was only February that the flatpak controversy happened. The effects of it haven’t even really been felt yet. The war for a universal app distribution format continues pretty actively.
I’d definitely encourage you to continue to fight for the causes you are representing here though. I will gladly live in a world with you where everything standardizes around using AppImage. There are pretty powerful forces who do not want that though and want things to stay exactly how they are and it’s of course the distributions/flavors that are benefiting from the status quo which is hardly surprising.
We can only take on these issues a day at a time though. If you can get Ledger to distribute more universal rules (and they are already offering an AppImage fortunately) then that’s one step closer to making Linux (especially on the desktop) more palatable for ordinary users. I also think the security implications you have spoken of are important. If things continue to move in the AppImage direction I may very well find myself using a source-based distribution at some point.
Thank you for all your feedback as well and for working on this and actually contacting the Ledger team to add these to their rules file. I and the blog support this cause. I also love that if Ledger actually adds this since I’m recommending their rules it will naturally “fix” my article for these distributions since the missing rules in question would just be in the same file I’ve been recommending.
Take care!
> I mean the rules are from Ledger. They are available here. The description from Ledger:
Yes, I meant those, as well.
> By a small subset of Linux distributions I assume you mean the most popular ones such as Ubuntu / Debian / PopOS?
None of those three rank in the top five on the Distrowatch popularity ranking (admittedly an imperfect measure of actual use), though two of them do have significant history and mindshare (and by extension, influence in the way to “do things” on Linux).
> What Linux are you using here? I bet it’s going to be Arch.
Nice try, but wrong (I use a source-based distribution).
> I’d say if you are using Arch you should always assume that you are going to need way more configuration steps than everyone else.
Without going into a long rant (especially since making broad statements in this area would definitely represent going outside of my areas of expertise), I will make two claims.
1. Many desktop Linux distributions have moved to an almost Windows-like “convenience” approach to security (installing and starting more services automatically, for example). While I don’t know have broad knowledge of the methods used by many of those distributions to secure resources from hostile “users” (meaning every account in /etc/password, and not necessarily real people), on the surface, it would appear that granting access to hidraw devices (instead of everything USB), and restricting that access to users in the plugdev group (potentially) represents a more secure solution. Obviously, crypto wallets require an extremely high level of security.
2. More important (and easier to explain), a more general solution (that works everywhere) should rank ahead (in terms of preference) of a less general solution (that depends on speceficity of certain characteristics, even if relatively common).
> Nevertheless thanks for sharing this for those who may be using one of those types of flavors!
Yes, I wanted to make this solution easier for others to find. Even Ledger support wanted to know how I eventually solved the problem, as they apparently have a significant number of customers of that their own rules don’t work with.
Hey name,
Those are some fair arguments. I’ll clarify a bit that should help some. Does it take a .deb package / have dpkg installed? That is what I meant which means Mint would be included as well as MX Linux (#1).
You know how when you go to web sites to download applications for Linux and it’s almost always a .deb package and sometimes a .rpm? Those are the ones I mean by the ones everyone uses. It’s a bit more than mindshare. If you aren’t using a source-based distribution (and I would still argue that most people aren’t but a lot of people are and have their reasons, good ones even) then almost everything that gets distributed is going to target those more convenient distributions.
Arch is traditionally a source-based distribution (although there seems to be a lot of packaged stuff these days but maybe that’s mostly for SBCs) so I’m not surprised. I was pretty close.
I will agree with you on your arguments about the Windows-like convenience and security. You’re right on this count 100%. I’ll even admit my distro since you admitted yours: I am using PopOS. When I originally wrote this guide though I was using Ubuntu. There’s no question you’re right that tradeoffs have been made to make it more convenient to use (and I would say the Windows-like description is spot on). I like those tradeoffs as I switched *from* Windows only a few years ago to using full-time Linux on my desktop (although I’d been doing Linux server stuff forever).
I definitely respect your passion for wanting to share this fix and I’m sure this will actually probably help hundreds if not thousands of people over time. I also respect your arguments and the way you made them. 10 / 10 would argue with you about Linux flavors again and you’re always welcome!
The udev rules don’t work for me (they don’t address /dev/hidraw at all, which still lacks access permissions). Perhaps they work on a small subset of Linux distributions, but this rule (for the Nano S Plus) should work on any distribution (that uses a plugdev group for access to USB devices):
KERNEL=="hidraw*", SUBSYSTEM=="hidraw", ATTRS{idVendor}=="2c97", ATTRS{idProduct}=="0005|5000|5001|5002|5003|5004|5005|5006|5007|5008|5009|500a|500b|500c|500d|500e|500f|5010|5011|5012|5013|5014|5015|5016|5017|5018|5019|501a|501b|501c|501d|501e|501f", TAG+="uaccess", GROUP="plugdev", MODE="0660"Hey name,
I mean the rules are from Ledger. They are available here. The description from Ledger:
udev rules to support Ledger devices on LinuxBy a small subset of Linux distributions I assume you mean the most popular ones such as Ubuntu / Debian / PopOS? The ones most people use?
What Linux are you using here? I bet it’s going to be Arch. hidraw is not even something I needed rules for at all. Do you know why I’m guessing Arch? Because I googled for “hidraw udev rules” and Arch seems to be the only Linux I can find that this is going to be an issue in.
I’d say if you are using Arch you should always assume that you are going to need way more configuration steps than everyone else. This comes up in a lot of my guides and your distro is always going to be ultra hard mode. It seems to be popular on a lot of SBCs I cover too and people always have the most trouble with it by far.
Nevertheless thanks for sharing this for those who may be using one of those types of flavors!
Thank you so much for posting this solution!
Hey ged,
No problem at all, thanks for leaving this! I just used it myself a few weeks ago on a reinstall and was glad I wrote it for my own sake instead of having to track this down again.
Enjoy and take care!
Thank you! Thank you! Thank you! I had a feeling it had somethig to do with udev rules. I was running it with sudo until I updated to the latest verison 2.50.1 which fails to load. These udev rules saved the day. Cheers!
Hey Helipil0t,
Excellent, I’m so glad it was able to help! I wrote it because I had the exact same experience and wanted to make sure I documented it for my own sake as I had to dig to find it.
Enjoy and take care!