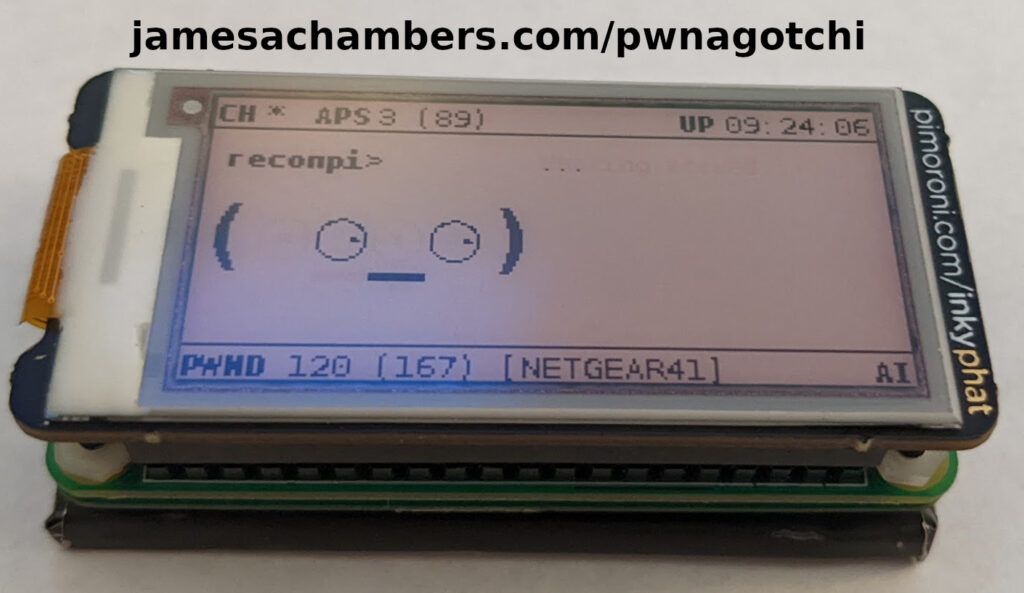
A “pwnagotchi” is a device used for wireless security auditing / hacking that captures the handshakes of any WiFi access points in range of the device. These handshakes can later be cracked. How difficult these are to crack depends on how secure the wireless network is. If the network is set up with the latest encryption standards and an extremely secure password (or is using WPA encryption) it can be nearly/essentially impossible. If the password is a common dictionary word it may crack within seconds.
It’s common and smart security practice for both enterprises and home users to check what kind of networks are operating within range. It’s common to find devices that are “broadcasting” a wireless access point used to share internet but this is often not intended / authorized. It’s also very common to find devices using extremely insecure passwords that will crack in seconds that are authorized to be on the network but need a more secure password. These are basically backdoors into your home / company and they can go for a long time without being caught when this is never checked for.
The “pwnagotchi” tool automates this process. It will capture anything in range to be easily checked later for extremely insecure hashes (typically using hashcat or there are even online tools to find common hashes which we will cover). This saves a ton of time and can greatly improve your security. Today I’ll cover how to build a pwnagotchi setup as well as the steps to use it. Let’s begin!