
P4wnP1 A.L.O.A. is a tool for the Raspberry Pi Zero W that allows you to plug a Pi into a host computer and send remote commands and share networking with a host computer all without any user interaction. A.L.O.A. stands for “A Little Offensive Appliance”.
The device is connected as a HID keyboard/mouse as well as a network interface to accomplish this. The device is automatically configured and does not require any special driver installation. It supports Windows / Linux / OS X. There’s practically no defense to this type of attack other than physically securing your USB ports.
The ALOA version is a successor to the original P4wnP1 which is still a very popular tool to use with a Raspberry Pi Zero W. The old version was very simple and could only deliver a payload and was basically a Pi version of the old “Rubber Ducky”. This is the alpha 1.0 release so there’s still some work to do to make things smoother and easier but this version is functional enough to start playing with.
ALOA aims to do much more than its predecessors by having trigger actions and multiple scripts ran based on those triggers. This allows you to adapt to changing environments and execute much more sophisticated actions.
On top of this, it is also a full Kali Linux distribution giving you all the power of Kali. This guide will help you get it installed and start experimenting with it. Let’s jump right into it!
Hardware

The Raspberry Pi Zero W is the wireless-capable version of the Pi Zero. It has a much smaller form factor than a full size Pi making it ideal for use in projects that benefit from a very small form factor while having a fully capable Linux PC.
Links: Amazon.com*, AliExpress.com*, Amazon.ca*, Amazon.com.au*, Amazon.co.jp*, Amazon.co.uk*, Amazon.de*, Amazon.es*, Amazon.fr*, Amazon.it*, Amazon.nl*, Amazon.pl*, Amazon.se*, Amazon.sg*


The SanDisk Extreme A1-A2 SD card has the best scoring SD card on Pi Benchmarks for years and is second in popularity only to the SanDisk Ultra (often included in combo kits). The application class (A1) means random I/O speeds (very important when running an OS) have to meet a higher standard. There’s no benefit on the Pi for A2 right now so get whichever is cheaper/available.
Links: AliExpress*, Amazon.com*, Amazon.ca*, Amazon.com.au*, Amazon.co.jp*, Amazon.co.uk*, Amazon.de*, Amazon.es*, Amazon.fr*, Amazon.it*, Amazon.nl*, Amazon.pl*, Amazon.se*, Amazon.sg*
Kali Image Getting the Image
UPDATE 3/18/2021: The Kali specific P4wnP1 image is no longer available and doesn’t appear to be distributed anymore but an updated version is available. Details below.
The good news is after a couple of years of very little activity on the project’s GitHub page the original developer mame82 released an updated version of the image
Grab the latest image for Raspberry Pi at the project’s GitHub releases page (the developer is now using the handle “RoganDawes” so if you see this don’t worry you are still in the right place):
Official P4wnP1 Releases GitHub Page
Download the img.xz file for the latest release (v0.1.1-beta at time of writing released 2/6/2020).
Write the image to your MicroSD card using your preferred method! The best way is to write a custom image using the official Raspberry Pi Imager utility but Etcher or even writing the image with dd will work.
Getting Started
There are several ways to connect to the Pi. My preferred way is to plug it into my computer and use the web interface / SSH to connect to it. I can then have the Pi connect to my home wireless and have an internet connection on Kali.
Plug the Pi into your computer. If you are on Windows you will see a interesting notification that Windows is installing and configuring drivers for a “P4wnP1 by MaMe82”. We can change this later to whatever we want but it’s a good sign for now that everything is working the way it should be.
Once initial configuration has finished we can now connect. Open a new tab in your browser and connect to:
http://172.16.0.1:8000
This is the P4wnP1 ALOA web configuration interface. From here we can easily start configuring the device and begin to play around.
Network Configuration
Let’s start by configuring your wireless interface so the Pi gets an internet connection. Go to the “WiFi Settings” tab. This is what you will see:
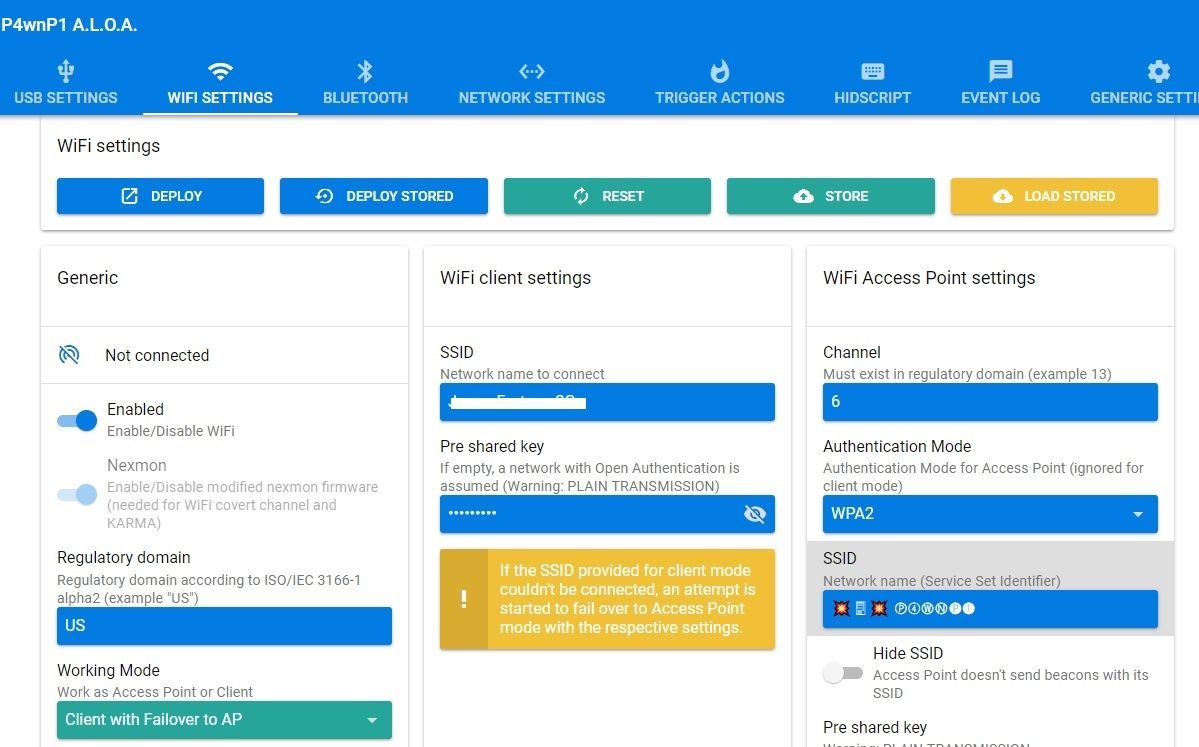
In the bottom left of your screen click the “Working Mode” dropdown and change it to “Client with Failover to AP” like I have in the screenshot. The WiFi client settings will appear in the middle of the page and you can enter your home network information. Now hit the “Deploy” button in the top left and the Pi will apply your settings.
Failover mode means that if the Pi can’t find or connect to your network it will start listening as an access point again. This makes it very easy to connect to the web interface when you take the device outside your home as it will fail to connect and start listening.
The SSID and pre-shared key to connect to the Pi wirelessly are along the right side of the screen. It comes prepopulated with a SSID of: 💥🖥💥 Ⓟ➃ⓌⓃ🅟❶ and a password of “MaMe82-P4wnP1”. You can actually completely configure the Pi without connecting it to the computer by just connecting to the SSID wirelessly. It is possible to get internet through the host computer the device is plugged in to but it requires additional configuration on the host PC (we’ll cover that later).
In addition to the wireless tab you have the network settings and bluetooth settings tab. You can click around these on your own as they are pretty self explanatory, but I will mention that it is also possible to configure the device through the bluetooth connection. Depending on the type of scripts you want to run it may serve you better later to connect over WiFi or Bluetooth so it’s good to know it’s there.
USB Settings
Go to the USB settings tab next. This is where we can configure the behavior and identity of our device for when it is plugged into a host.
On the left hand side of the screen you can configure all of the settings that control how the device identifies itself to the computer. You will want to change these because “P4wnP1 by MaMe82” is hilariously suspicious and likely already being detected by AV software. Pick some custom settings and make the device your own!
On the right hand side of the screen we have the gadget mode configuration options. The top two options (CDC ECM and RNDIS) are network interfaces that the Pi uses to communicate to Windows/Linux/Mac.
The middle options are related to HID. HID stands for Human Interface Device and appears to the computer as basically a mouse or keyboard. This is how P4wnP1 is able to send keystrokes and mouse movements to your computer. The computer thinks it is actually talking to a keyboard instead of our Pi.
At the very bottom you have a “USB Mass Storage” option which can mount a CD-ROM iso or a emulate a small flash drive.
HIDScript
Now that we understand that the Pi is impersonating a mouse and keyboard let’s go to the HIDScript tab and start having some fun. This is where we can write and load scripts that tell the Pi what to make the host computer do.
Press the “Run” button. A script will run that will open Notepad and tell you Hello from P4wnP1 and move the mouse around. Notice on the right side of the screen you can see the job running with a red X next to it. You can cancel jobs here by clicking the X. This also has a log of jobs that have been ran and whether they succeeded or failed.
Now try running some of the other examples included with the alpha release. There’s a lot of different programs including a “game” that opens mspaint and has movement keys to move around with. There’s a lot in these examples to help you build a HIDScript to accomplish what youa re looking to ultimately do with the tool.
Trigger Actions
Trigger actions one of the key features of the reboot of this tool. HID scripts stem from the original Rubber Ducky tool that simply ran a script to deliver a payload when inserted into the computer. Although the payloads have got far more sophisticated over the years the way they work (and the limitations of it) really haven’t. They deliver a weaponized payload and that is it.
With trigger actions you have a chance to respond to specific triggers with specific actions making it more like an application or framework. Let’s look at some of them below:
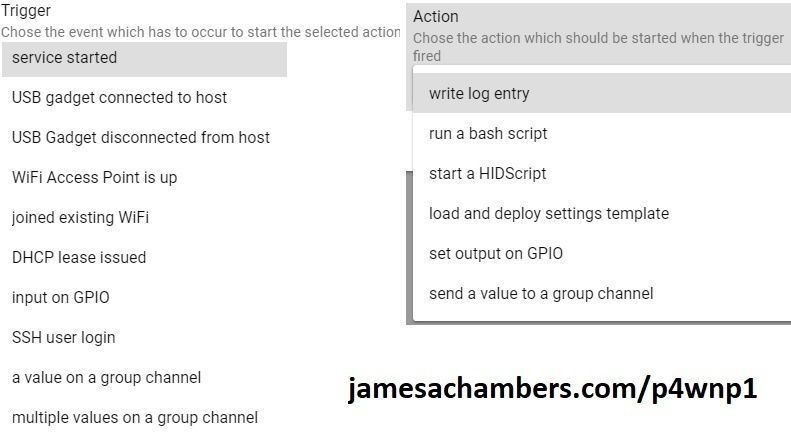
We can see a lot of very useful triggers such as “service started”, “USB gadget connected to host”, “SSH user login”, etc. The actions are very powerful. You can trigger a bash script, run a HID script to send a second/third/etc set of inputs, and even setting output on GPIO.
With this model your Pi can actually have a conversation with the host. You have the chance to react differently to different situations that may arise during execution on different hosts. This is more like a dance than the previous payload delivery model.
Accessing Kali
Of course you still have all of Kali Linux available to you from the Pi Zero. The easiest way to access them is to SSH in.
To connect with SSH simply connect to the same address that we used to access the web interface on port 22.
ssh 172.16.0.1
Log in with the default credentials of root / toor and you will be on the command line of Kali. If you connected to the internet by connecting to your WiFi via the web interface you will also have internet access from the Pi and be able to update.
I recommend doing a apt-get update && apt-get upgrade to get all the latest packages and fixes. The author says in the README that apt-get upgrade should not break anything related to P4wnP1 and I was able to do it successfully.
You may also install the full Kali Linux suite by typing
apt-get install kali-linux-full
This will download all available packages for Kali Linux giving you a complete full installation on your Pi Zero!
Templates
P4wnP1 has a feature that wraps all necessary HIDScripts and settings together called templates. This makes it easy to switch between different configurations without having to go change all the options one by one.
The example that ships with P4wnP1 ALOA alpha is the WiFi covert channel attack. This is basically a port from the original P4wnP1 script of the same name and function.
The attack launches a PowerShell window on the host and transfers/launches a script payload that allows you to control the host by connecting to the P4wnP1’s WiFi. This very powerful attack actually allows you to remotely control “airgapped” computers that aren’t connected to a network since the Pi itself becomes a wireless access point.
Deploying this attack is as easy as loading the template and pressing “Deploy”. Note that you cannot connect through ssh on USB while running this attack since the USB interface is busy communicating with the host. You need to connect to the WiFi specified in the P4wnP1 wireless settings tab and then you can reestablish your SSH session.
Before you hit “Deploy” make sure that the HIDScript for this attack has the right language for your country. The default for this one is US but if you have a different keyboard layout change it to your country in the HIDScripts tab.
After plugging in the “Deployed” state USB connect to the P4wnP1 WiFi access point and type the following to open the screen session that allows you to inject your keystrokes:
screen -d -r wifi_c2
Make sure to check out the following folders for more goodies:
P4wnP1 Bash scripts:
/usr/local/P4wnP1/script
P4wnP1 Legacy tools:
/usr/local/P4wnP1/legacy
Benchmarking / Testing Storage (Optional)
If you want to verify your drive’s performance you may want to run my storage benchmark with:
sudo curl https://raw.githubusercontent.com/TheRemote/PiBenchmarks/master/Storage.sh | sudo bash
If you search for the model of your drive on Pi Benchmarks you can compare your score with others and make sure the drive is performing correctly!
Conclusion
P4wnP1 ALOA is looking to evolve the tool’s capabilities past the previous version with trigger actions. It also aims to streamline the way these scripts are written in by moving code into pure Javascript rather than Ducky code. ALOA is much more similar to an application framework than a one-and-done payload. Indeed, the developer MaMe82 has this to say in his readme:
P4wnP1 A.L.O.A. is not meant to:
-be a “weaponized” tool
-provide RTR payloads, which could be carried out by everybody, without understanding what’s going on or which risks are involved
P4wnP1 A.L.O.A. is meant to:
-be a flexible, low-cost, pocket sized platform
-serve as enabler for tasks like the one described here
-support prototyping, testing and carrying out all kinds of USB related tasks, commonly used during pentest or redteam engagements, without providing a finalized static solution
-Mr. MaMe82
Some of these statements he makes here are a bit much. It’s not meant to be “weaponized” but it’s still called “P4wnP1″ and has the hilarious SSID title of”💥🖥💥 Ⓟ➃ⓌⓃ🅟❶ ” featuring emojis of a device exploding. Give us a break MaMe82!
But I really like his final point he makes in the quote. This framework can be used to carry out all sorts of USB tasks in a way we haven’t seen before. It may not be too long before we start seeing USB drives capable of running many different actions based on triggers that are unique to each environment.
There’s a lot more to know about P4wnP1 ALOA so make sure to visit the tool’s documentation located at: Official P4wnP1 Documentation Page
The documentation is very lengthy but with this overview it shouldn’t be as overwhelming as the first time I went through it. Have fun!
Other Resources
If you have a Raspberry Pi Zero you may want to check out my Kali P4wnP1 Linux guide here
If you have the 7″ official Raspberry Pi Touch Screen TFT display then check out my 7″ TFT for Kali guide





So I have installed the newest Callie install from the official GitHub repository for this project. P4WNP1 I flashed it on my SD card. I plugged it in, and it came up as an unknown network. Then I entered the IP and port number and found the dashboard. Here is where the issue lies. I can access the dashboard with it plugged in, but it does not produce a network to click on, even though it says it’s enabled and everything through the dashboard. I’ve been trying to fix this for two days. Don’t know what’s going on.
Hi James,
Great guide.
I am having some issues getting SSH to work with Kali Linux P4wnP1 ALOA .
I am using a Raspberry Pi Zero (basic, not W) connected to my Macbook, and I have managed to SSH into the normal RaspbianOS with some tinkering with some Files on boot.
However, I cannot seem to manage to ssh through Ethernet over USB with Kali Linux P4wnP1 ALOA.
Should I modify any files in boot or should it work out of the box?
Thanks
Marc
Hey Marc,
Great question! I have struggled with this in the past as well and it usually ended up being that the Pi was going into the wrong “mode” depending on what was plugged into it and how it was interfaced. When it detects it’s plugged into a computer it should go into “gadget” mode and then this type of connection is available.
A couple of things to check. The first thing is you have to have a Pi Zero or Zero W. The other Pis don’t support gadget mode. Next make sure you are using a cable that supports both data and power. This is surprisingly common to have micro USB cables that are charging cables only and aren’t data capable. This type of cable will still power the Pi but it will not see the computer and will boot up in the regular “mode” and won’t show up in device manager or be seen by the computer. I eventually found a charging/data cable for a old Samsung Galaxy phone back when they still used micro USB and that one gave me the data connection and would cause the device to show up to the computer as a Linux gadget.
If you are on a Windows PC pay special attention to “Device Manager” when you plug in the device. The window should start refreshing when you plug it in and you should see it show up as either something like a “Linux gadget”. If your device is not in gadget mode it will usually not show up at all if it’s just getting power. There’s also a “mass storage device” mode that can be activated where it shows up as an external drive and lets you transfer files.
Check out this document here. This is an extremely detailed step by step specifically on setting up the Ethernet connection to work with Windows (and even get internet access, but you don’t have to go that far if you don’t want to, you just need the basic connection working for SSH). Definitely let me know what you find and how it goes!