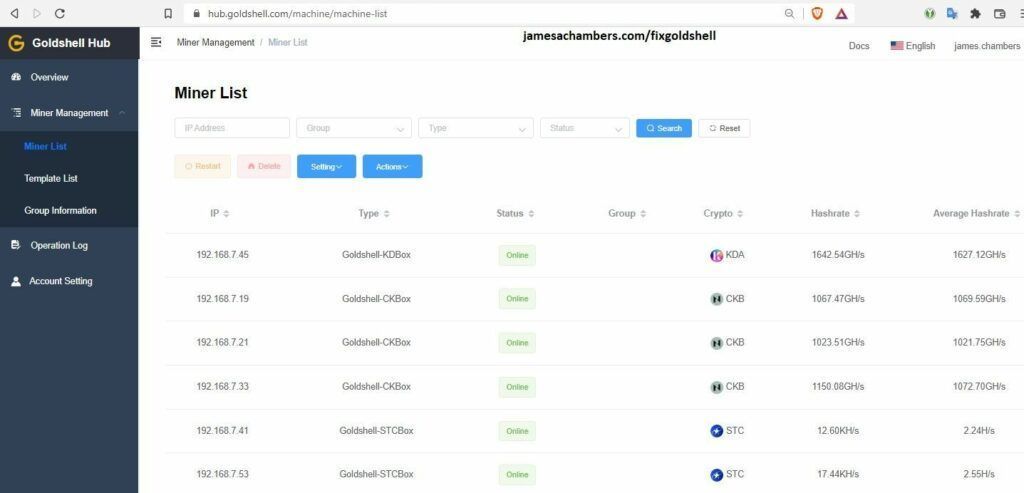
Recently Goldshell released the 2.2.0 update which includes the new “Goldshell Hub” (featured above) which is basically a cloud control center for your miners. I was able to upgrade 23 miners successfully but I had one Mini DOGE and one ST-BOX fail during the upgrade.
After a substantial Google journey and finding some very helpful posts on reddit I was able to recover both of them without waiting for Goldshell’s response on the situation. I will cover what I used to do so and where to find them in the guide but it is at your own risk and if you aren’t outside of your warranty support period you should almost certainly contact Goldshell instead. Even then it might still be worth a try because it wouldn’t surprise me if they hand out these images like Halloween candy even if you’re out of warranty.
With that caveat/warning given, I have 25 of these miners and only 1-2 were bought directly from Goldshell in the first place so I was not worried about losing my warranty or support period from them but you should be careful here and only proceed if you understand this. Let’s begin!
Diagnostic Lights
After I initially tried to upgrade to 2.2.0 using the Goldshell web interface 23 / 25 miners upgraded fine. One Mini DOGE however started blinking both the red and blue light very briefly every couple of seconds. It had network link lights for a few seconds upon startup and then it would go dark other than the 2 blinking indicator lights.
The Starcoin miner on the other hand permanently illuminated both the red and blue lights and stayed stuck on. It also had network link light activity (that never stopped) but it never acquired an IP address.
If you are seeing one of these two conditions it’s likely your firmware is stuck in a broken state (especially if this happened during/after a firmware upgrade like mine did).
Recovery Process
The process to recover from an event like this will probably not be surprising if you have owned other ASIC miners. We need to flash the firmware using a SD card flashed with a recovery image.
Unfortunately Goldshell does not publicly post these images on their GitHub page like they do with the regular firmware. They certainly should though as they are incredibly useful and it only took a few minutes to fix the miners once I had all the right pieces.





Hardware Requirements
The Goldshell box miners have an empty SD card slot on the back of them. You need to have a blank SD card to write the recovery image to.
Here’s a recommendation I frequently give for Raspberry Pis if you don’t already have one:

The SanDisk Extreme A1-A2 SD card has the best scoring SD card on Pi Benchmarks for years and is second in popularity only to the SanDisk Ultra (often included in combo kits). The application class (A1) means random I/O speeds (very important when running an OS) have to meet a higher standard. There’s no benefit on the Pi for A2 right now so get whichever is cheaper/available.
Links: AliExpress*, Amazon.com*, Amazon.ca*, Amazon.com.au*, Amazon.co.jp*, Amazon.co.uk*, Amazon.de*, Amazon.es*, Amazon.fr*, Amazon.it*, Amazon.nl*, Amazon.pl*, Amazon.se*, Amazon.sg*
Software Requirements
First grab Etcher if you don’t already have it (we need this to write the image to a SD card).
Next make sure you have 7zip as we will be decompressing a couple of archive types that the native Windows tools won’t work on. If you have WinRar or an additional compression tool already beyond the native OS tools you should be fine.
Recovery Image
Next grab the Mini DOGE recovery image from one of the shared links that we have:
Goldshell MiniDOGE 2.1.1 #2 (Alt)
Goldshell HSBox 2.2.3 (thanks smashthestate from reddit)
*UPDATE*: Goldshell responded to my ticket with the Mini DOGE 2.1.2 recovery image and the STC Box 2.1.6 recovery image. They didn’t tell me not to share them or seem at all concerned about it (maybe not that many people ask for these and that’s why they aren’t posted) and it may save someone else’s bacon:
Additional Documentation (Official Goldshell video and tutorial .docx):
Official Goldshell Flashing Tutorial
Special Note on using Mini DOGE firmware on other models (temporarily to recover)
But wait, I don’t have a Mini DOGE, you might say. Well fortunately the Mini DOGE version seems to at least boot up enough to flash the real STC Box firmware. I doubt anyone other than Goldshell will have the link to the STC Box specific firmware as it was a limited run of only a few thousand miners.
It doesn’t really matter in this case as all we are going to use it to do is get the box to boot up again so we can flash the correct firmware on it. Ideally we would have the correct firmware. If this part scares you then for sure contact Goldshell for the right link for your miner.
I did not try anything else as I haven’t had any other types fail yet than the STC-Box and the Mini DOGE. It’s possible that it might not work on some or even cause some sort of problem (unlikely in my opinion unless you try to start configuring it or mining with it but it’s a risk) on other versions. I honestly wasn’t sure if I would brick it or make it worse but my educated guess as someone who does a lot of work on embedded systems my guess was all that would happen is that the image wouldn’t boot (which is exactly where I started).
What happened for me is that it booted up and actually did think it was a Mini DOGE. I did not try to do anything else and you shouldn’t either. It’s the wrong firmware for the miner. Literally nothing good can come from trying to do anything with it in this state other than flash it with the right firmware as quickly as possible. Do not try to add a pool, don’t change the default password, do not do anything else basically. Sign into the miner with the default “123456789” password and upload the correct firmware for your miner to the Box.

Flashing the Firmware
Now that we have all the pieces let’s actually flash the firmware. Make sure you have extracted “Please unzip this file-MiniDOGE-2.1.1(1).tgz” twice. The first time you will get a .tar file. Extract the contents of that .tar file and you should end up with:
burn-Goldshell-MiniDOGE_MCB_V5_4-2.1.1.img
This is the file we are going to select with Etcher (note that it starts with burn- to tell us this is the right image to “burn” to the SD card). Now insert your micro SD card into your computer and Etcher will write the image to the card. This is typically pretty fast.
Now disconnect power from the Goldshell miner if it happens to still be turned on. Insert the SD card into the SD card slot. Be gentle. My miners had SD slots that had a spring-loaded SD mechanism that “clicks” into place. That means that the SD card will not go all the way into the slot. To remove the SD card you actually push in again and you will feel it release the spring and the SD card will be pushed out most of the way for you (safely). I have seen this confusing some people.
If you happen to put the SD card in and the SD card reader’s “switch” is already locked in the back position just keep pushing gently and you should feel it unclick. Once this is done you can push it all the way in and you should feel it “lock” into place correctly until you push once again to release it when you’re done.
The process does not take long. Maybe a minute or less. After 20-30 seconds you will see the light activity (usually the red and blue one together or whatever) turn to just a single blue light that periodically flashes. This means it’s done. Disconnect the power and remove the SD card. Now power up the miner again and with any luck it should boot up into the Mini DOGE firmware.
Now flash the correct firmware for your miner immediately (as I’ve said before) without doing anything else and it will finally boot up and be ready for configuration! Remember to check https://find.goldshell.com as the IP settings for the miner will have been wiped so the IP address will likely have changed on your network.
Further Troubleshooting
Flash not completing
During the update to 2.2.1 one of my wife’s Mini DOGE units failed. I tried flashing it with the recovery image and it failed several times. I was so confused because the lights were blinking correctly but the flash would never finish. If I took out the SD card in the middle of the never-finishing flash the lights changed to indicate that the flash was interrupted and it wouldn’t boot correctly afterward no matter how long I had waited (although it did behave differently with both lights stuck on and network link activity but no IP).
The problem turned out to be in the most unexpected of places. It was the previous partitions on my SD card. You might think that Etcher actually clears all of these out and completely formats the disk. You would be wrong and I’ve seen this before with Raspberry Pi stuff (it’s why I recommend using the Pi Imager tool for Pis and not Etcher).
The fix is to run the SD card association’s official tool to completely (and really) blank the SD card. The tool is officially available free of charge (courtesy of the SD Card association which is basically a cartel of SD card manufacturers that manage the standards but the software is great): Official SD Card Association Formatter Tool
Run this utility on your SD card in “Quick Format” mode (enough for mine but some weird previous partition types like zfs might need a full overwrite) or you can do “Overwrite format” to do a full drive overwrite (zero’ing out the free space) if you want to nuke it (it’s the only way to be sure). This is even necessary on Pis sometimes when the Pi imager can’t even fix them. In those cases the SD card association’s tool is the only thing that seems to help (previous zfs partitioning is an example we’ve seen here on the site).
Now write the image again on the now truly blanked SD card using Etcher and with any luck it will finish the entire process within about 15-20 seconds that time as it is supposed to take.
Reseat your SD card
It is very easy to unseat or not properly seat the SD card in these slots. One tip with these is to let the SD card slot do the work for you. Push the card in and when you start feeling resistance just let it gently guide the SD card into place and it will click. Don’t fiddle with it at this point as if you try to start pulling it slightly out it will let you do that and it will be unseated (as well as leave the SD card slot in the back of the port, it will not come out as you pull out the card). If you want to remove the card (and you should if you’re reseating it) then actually push it further IN and the slot will push the card back out for you.
If you pull the card out the SD slot will remain locked in place in the back. If this is the case just push the SD card in manually all the way in until it hits the back of the SD card slot and you should feel it push and release and it will spit the card out about 50% and be back in the correct position this time for you to insert it again normally.
There’s nothing “locking” it into place when it clicks (it’s the slot itself clicking, not actually your SD card) which is why touching it is generally bad once the slot is in it’s final position. Even something bumping or brushing up against the slot is enough to unseat the card and lose pin contact with a design like these SD card slots have (not meant to be used except for recovery so it’s understandable).
You may need to reseat it a couple of times if it’s an older SD card with a lot of wear. These tend to not make as good of contact with the pins. Reseating it and trying to keep the edges lined up as well as possible will often get these going.
Conclusion
I was back up and running within 24 hours and I would have been back up and running within 5 minutes if I had these files.
I hope Goldshell releases them publicly as it’s not ideal to not have the exact right firmware and is why it is a little frustrating that Goldshell hasn’t publicly posted these recovery images (like they have with the regular firmware updates in their GitHub repository). Maybe I’m spoiled as these are generally available from other competitors without contacting support.
Hopefully they will release recovery images on their GitHub in the future and then I can recommend you download the exact right model. Try to get as close as possible if you can but in my experience it worked on the STC Box which seems more different from the Mini DOGE than the other ones (it only uses 60W and mines a Cryptonight-R variant).
If any of you have additional links/tokens for other miners from Goldshell and want to share them in the comments I will add them in the links section. Definitely let me know if you successfully try it on some of the other models I haven’t as well! These links weren’t easy to track down for sure and they don’t seem to expire. Let’s see if we can collect (catch?) them all! UPDATE: You will need to contact Goldshell for any more up to date images. I’m no longer supporting these as I was never able to succeed in getting the mining community to share these thus you guys are on your own.
Hopefully the links / guide are able to help some of you as well!
Other Resources
If you are lucky your miner may just have lost it’s IP address. The diagnostic lights should help to diagnose this condition. A great tool to check for this is Goldshell’s official “Yotta BC” which I wrote a guide for here: Bulk Management of Goldshell ASICs using YottaBC
For the best place to mine and exchange your altcoins check out my Best Altcoin Mining Pools and Exchanges article
To understand the current situation with Ethereum mining and when it is ending see my Why GPU / Ethereum Mining Is Toast – Stop Buying GPUs article




İ have kd6 miners with portforwarded.goldshell@stratum+tcp://aminingpool.com:3334 problem.
How can i find recovery image? Anyone has it?
İ can not update from Console using standart update method.
Hey Mehmet,
I’ve tried to get that one before and someone said they were going to send/share it after they got it from Goldshell. They did not. In fact nobody has shared any for quite some time. We have literally 0 of any of the new KDA miners. The mining community is what it is and it’s honestly dying / a shadow of it’s former self anyway.
They had 0 interest in all of my published security research about all the vulnerabilities which would *NOT* have been the case a few years ago. I was pretty naive to write this thinking it was still 2017 or something. Nobody cares unless it’s their miner, right? There isn’t really that kind of a community anymore and I’m probably one of the last people that remembers there ever was and my articles would have fit right in a few years ago.
It’s definitely dark times. I’m afraid you will almost certainly have to contact Goldshell and wait for their support. Let them know if you aren’t happy about this. I wasn’t able to get them to change their policy or get very many people to share the images unfortunately!
To put it bluntly the mining community are losers now and they have been for years (it was when they threatened to 51% attack Ethereum which nobody else probably remembers or won’t admit they do that it became clear they were too far gone). Literally this happened to someone else already with that exact model that didn’t share it and there’s probably 12-20 people that didn’t comment for every one of those that did. The mining community is only as good as we make it and it turns out that’s never been worse.
I’m sorry that nobody would share this. It does bother me but you can see exactly how we got here (and it probably won’t really surprise you but I hope it disappoints you). That is a decision other people made that is going to cost you money.
I predict that nobody will do anything about it whatsoever and this will continue to get worse. Manufacturers will continue to cover it up and miners will continue to ignore it (until it comes to them). I wouldn’t have predicted it before but I’ve learned the hard way now. The experiment has been ran and is documented here and you can see exactly how that went unfortunately. I was writing for a mining community that doesn’t exist anymore and hasn’t for a long time but I still wish it did.
I have the exact same issue. I just received mine today. It will not accept any mining pools I enter and it defaults back to the portforward pools. I tried updating the firmware but it won’t complete the task. I have factory reset several times to no avail.
Yes, that won’t work. You need to flash the recovery firmware using a SD card. Your miner has a virus and the hacker isn’t going to let you flash it which is not surprising in the slightest.
That is what this article is about. Flashing your miner with the SD card recovery firmware. A factory reset will not do anything to it. This is well known.
This person never came back and shared the firmware so if you have their miner you are going to have to contact Goldshell and wait for the firmware. They cannot and will not help you. They already had their chance and they got theirs and washed their hands of the issue. If you would come back and share the link though once you get it you can break the cycle you can make a difference!
Well as u can see if you open the canaan firmware list you will find that A1246 section is empty for some reason.
And ofc if they happen to send the kd6 image ill be sharing it here no worries man
Hey Louis,
I do see that for the A1246 in there. That is strange. It looks like it’s pretty hard to find and people aren’t happy about it.
From what I have heard and seen Avalon’s support is *terrible* especially compared to Goldshell’s who honestly have the best in the industry. They may be significantly harder to contact. I don’t know if you bought the miners from them but if you did that should get you some kind of support.
I did some searching to see if anyone posted a link and the closest I came was those reddit threads where people said they eventually got it but that Avalon’s support sucked (or some variation of that). Some people seem to be saying the FMS tool they have on their site may be able to do it (maybe that one uses an online firmware update server or something?).
I’d like to take a moment here and restate my frustration with manufacturers who are playing games with the recovery images (including Goldshell). It’s dumb. I’m not sure if they are doing this to try to prevent people from finding security issues in their products or if they are doing it to try to control the secondhand market and make it a nightmare to get support if you didn’t buy them from them. It certainly didn’t help with their security.
I have unpublished security research on these devices. Here’s how bad the Avalons are for security (you can change the password on them without having any access as I will show here):
That’s it for the sneak peak at my unpublished security research on cryptocurrency ASIC miners but suffice it to say the security on these devices is *terrible*. I also have ones for InnoSilicon, JasMiner and a few others in that article. I’ve disclosed them to the vendors. Avalon is a vendor that didn’t respond (only Goldshell did).
They’ve never fixed this and probably never will until I publish my security research and their customers basically force them. I’m fine with publishing Avalon’s piece right now. I would have published the entire article at this point if Goldshell hadn’t told me they need more time to address these. It’s only for their benefit that it has been held back as I’m certain that none of the other manufacturers will ever respond.
Clearly other people have found this vulnerability like I have and probably even more (I noted in my article I definitely could have gone further if I wanted to backdoor these). I posted the research so you could see how easy it is for something like this to happen and that I wasn’t stack smashing or using any advanced techniques to find these holes in Avalon devices. Anyone with Burp Suite Pro could easily have stumbled upon them even with far less experience than I have doing this stuff. It was literally one of those textbook perfect examples of something you never actually see in the wild but theirs was literally as easy as changing GET to POST and changing the password to whatever you want (nope, don’t need to know the existing one).
Sorry I don’t have more answers on the Avalon as I don’t own one but they’re definitely very easy to hack so I definitely believe you and if Avalon tells you that this is impossible tell them they have no clue what they’re doing and that it’s not only possible but their devices are the EASIEST. I literally told them about this specific hack several months ago and they ignored it and I have no doubt they ignore any other security issues they know/hear about as well as I can personally vouch they ignored mine.
You are basically on the losing end of Avalon’s gamble that it’s more profitable/better for them to ignore these security issues and pretend it’s impossible despite it hurting their customers (as opposed to fixing the security issues and releasing patches/firmware updates). Definitely let us know how this turns out for sure!
The problem is my friend some of the ck5’s arent getting any ip anymore so i need to recover them (if possible) snd for the kd6 already contacted goldshell but still no reply
Ps: i do have avalons also with the same problem do you know any way to recover them as well? Thanks alot for your help man
Hey Louis,
The instructions I posted from the CK5 are exactly for if it won’t get an IP address basically. Those ones will reset with the reset button held for 7 seconds and I’d imagine that is what Goldshell will tell you to do for those ones but if they send you a recovery image and I’m wrong then definitely let me know (I’d love to share the links for them too, I’m trying to build a collection of all of them).
Avalon does post their firmware updates/recovery images here. I’d start with doing a flash on the Avalons with that software and make sure they are all running the latest version. Even if they are I would flash them again to make sure you flush out anything that may have made it into the miner’s memory.
Goldshell isn’t too bad about responding. I went through this same thing as you and so did a few others and most of us were too impatient to wait for Goldshell’s reply and ended up using another recovery imagine but they usually respond within about 24-36 hours. I feel like it’s almost exactly always a day and a half and then I will hear back from them.
These are always tricky to deal with but try using the Reset trick on the CK5s (I don’t expect this to work on the KD6) and I bet you can get those going again immediately. The KD6 I’d imagine you will be hearing from Goldshell today or tomorrow and if you wouldn’t mind I’d love to post the links to that image on here once you get them! I know it will be too late to help with your case (as it was mine) but who knows how many others it may help in the future to just have a copy available immediately (saves time and mining $$). Best of luck and let me know how it turns out!
Hello james your thread was really professional and helpful but i really need kd6 and ck5 recovery file cz my mining farm has been hacked like dave if u can helo thanks
Hey Louis,
I believe that the CK5s don’t have the same type of writable storage and only use SPI flash (only changes during firmware upgrades). I found some instructions to reset those. For that one you should be able to reset it back to factory by holding the button for 6 seconds:
That should fix the CK5s since they work a little bit differently than the smaller box miners.
I’m not sure about the KD6. That one very may well have storage like the boxes as I know some of the newer 6 series do have it and aren’t purely SPI flash storage. You can always try using one of the other recovery images to recover it (lots of people have done this in the comments here) but this is extra scary on a machine like a KD6. You may want to contact Goldshell for the image on that one but if you share the link with me I would gladly post it here as nobody has sent that one to me before.
Hopefully that helps!
Thanks James…. Really appreciate the help…
Hey Dave,
No problem at all, definitely let me know if I can help further!
James what is the fix for Portforwarding on goldshell mini miners?
I got hit on all of mine.. (9 of them)
Hey Dave,
Welcome! I’m sorry to hear it’s under those circumstances but I’m sure we can get it under control.
The first thing to do is determine how they are reaching the miner. At some point this miner was reachable from the internet meaning if someone types in your IP address into a browser they can get to the login screen of the miner.
The reason this usually happens is if people put a port forwarding entry on their router. This is usually done to access them remotely. These should be removed as basically they are bypassing the ASIC security and hacking your miner to varying degrees. You could set up safer remote access by setting up a VPN or even remote desktop on your main computer would be better than the ASIC miners directly.
Now let’s assume you’ve already done that. If you’re 100% sure that the ports are closed and your miners can’t be reached from the internet then one of them has a virus basically. Only one of them needs to have the virus and it will change all 9 miners. Basically this means that it doesn’t necessarily mean all 9 of them have it. Only one is needed and it will change anything else that is nearby / on the same network.
Now as for how to fix it you will basically do the SD card reimage in this guide. This is the same as reformatting / reimaging your computer to reinstall Windows on a completely blank drive. This will clean the virus off the miner and restore the factory settings. Note that you can’t use the web interface to do this, you have to do the SD flash.
Which miners are we talking here? Best I can tell you can basically download the MiniDOGE or STCBox firmware from these links and use it to clean/reformat the miner. This will put the wrong firmware on it temporarily but once it is cleaned you will go into the web interface and flash the latest version of the correct firmware from Goldshell’s GitHub page (linked in the article).
We already had someone do this and successfully defeat the attack. You may have to do all 9 of them though because of what I said earlier about if it’s on just one it will change all the ones it can talk to (standard procedure for viruses/worms/bots unfortunately). Definitely check out the other person’s comment though on this thread as they had the exact same situation and solved it this way. Hopefully that helps and let me know if you need any more help!
James the flash worked on my miners!! 2 have been up now for 12 hours!! Doing the flash on all of them b4 putting them online!! Thanks again for the help!! Greatly appreciated!!! Stay well…
Hey Dave,
Congratulations! You definitely did it right doing the flash on all of them before going online. That way you don’t end up with a situation where ones you haven’t cleaned yet reinfect the others making you start over. Once they’re all gone it’s over. They have to be in at least one for this to continue.
I’m very glad you got it, take care!
STC Firmware is not for flashing, please upload again or send me via email XXX. Thanks
Hey Annop,
That error message sounds like it’s from the web interface. This type of firmware cannot be flashed through the web interface. There’s basically nowhere that can give you an error like that.
You’re basically supposed to put it on a blank micro SD card to flash it. There’s nowhere to give you an error like this unless you’re trying to do it in the wrong place. Make sure to follow the instructions in the guide or the ones from Goldshell I have linked to to try to flash these.
If you want the old web type of flash firmware you can upload through the web interface that is already publicly available at the GoldShell firmware GitHub repository. This is for miners that won’t boot up usually. Hopefully that helps!
I have same problem with you so I need to flash by using Image file but your link is firmware-Goldshell-STCBox-2.1.6.cpb. Please send me or upload image file again, Thanks.
Hey Annop,
The file when you click it should take you to the Goldshell help desk and download:
Please unzip this file-STCBOX-2.1.6.zipIt should be a zip file. This is for this link:
https://goldshellhelp.zendesk.com/attachments/token/42JDFGcoFkIwrKeGkrx5pFYyP/?name=Please+unzip+this+file-STCBOX-2.1.6.zipAs you can see I do not host the files. They’re links to Goldshell’s files.
I take it you are seeing the file inside the “2.1.6” folder. That is not the right one. You actually want to open burn-Goldshell-KDBox_MCB_V5_4-2.1.0.tgz. If you open up this file inside is a regular .img file “burn-Goldshell-KDBox_MCB_V5_4-2.1.0.img”. That is the file you will burn to your SD card with Etcher (similar to other miners like AntMiners as well).so it will boot again
I know it’s referencing the KDBox for some reason in the file names but that is how Goldshell has it. It probably just means that a STC Box and KD Box are not very different as far as the image goes and they’re reusing files that are the same on all Box miners. These are *definitely* Goldshell’s files though.
You can also use the Mini DOGE one to recover it and then flash it with the normal STC .cpb from Goldshell. I’ve done this before to recover miners I don’t have the image for just as a tip! I feel like I had to use the Mini DOGE one instead of the STC Box one to recover mine but in retrospect I think the reason is that my micro SD card needed the SD card formatter tool ran on it to completely blank it (it wasn’t doing anything in the miner until I ran that tool on it).
I covered blanking the SD card with the official SD card association’s free formatting tool in the article at the end if you end up running into this issue but I figured I’d mention that I actually used the Mini DOGE one to recover mine as I hadn’t figured out my other SD cards weren’t truly blanked. You should obviously not do anything with the miner when it has the wrong firmware on it after you initially flash it. We’re really just doing it that way to get it to boot again because then we can flash it normally through the web interface. Just log in with 123456789 and upload the latest STC Box .cpb file once the miner will actually boot again. Once it has the correct firmware you should be completely good to go!
You help me a lot, Thank you so much.
No problem at all, best of luck and let me know if I can help further!
It is Work!! I try Minidoge for SD card first and then upload STC 2.2.1 but I have a big problem if you can help, Everyday my pool change to portforwarded.goldshell@stratum+tcp://stc.ss.dxpool.net:9977, It is not mine so how to solve this, Please help.
Hey Annop,
Ahh yes I am familiar with this issue. I actually have an unpublished article about ASIC miner security issues across multiple ASIC manufacturers. Goldshell is actually one of the responsible ones that is working with me to fix these exploits. Last I spoke with them they said they are still working on them and needed more time. I am not going to publish the vulnerabilities until Goldshell has updates/fixes available as it would only make the botting that much worse.
The “portforwarded” part is giving us a hint. Port forwarding is forwarding a port from the internet / your router to the miner. When you do this you can type in your internet’s IP address and access your miner remotely.
The only problem with this is that everyone else can also access it remotely. If there are any security vulnerabilities in the ASIC miners (and it turns out there are many and I have personally discovered and disclosed a bunch of them to the manufacturers) the bots are remotely taking over your miner / changing the pool. Observe how easy these are to find on public web sites that scan the internet for port forwarded devices: Censys cloud-box Search
It gets worse though. Some older versions of the Goldshell firmware had OpenSSH remote access opened. This means that it’s possible for the smartest bots to backdoor your miner. Once this happens your miner basically has a “virus”. It’s literally just like a virus with a computer. The *only* way to fix this is what you just did / are doing (flash the firmware with the SD card, not the web interface as that won’t be good enough).
Now that we’ve covered that background I can tell you how to stop it. You need to remove any port forwarding entries to your miners out of your router. It needs to stay behind a firewall. If you need remote access set up a VPN or remote desktop or something that is better designed to withstand remote attacks because ASIC miners are terrible at it.
Nothing should be able to reach it because they do not have the security to withstand remote attacks. This will stop most of these bots right away. There are other bots out there too like the XAOBTC guy, there’s one that puts in the pools IDefault, etc. They’re constantly looking on sites like Shodan/Censys and others for miners that are port forwarded from the internet. This is step #1.
If you have removed the port forwarding entries and it’s still happening then that means the attacks are now coming from inside your network. That means like I was explaining earlier one of your miners is “infected” with a virus. I hate to say it but in this case if you are certain the miner is unreachable from the internet and it’s still happening you probably need to do the full SD card recovery on every single one of them. That will definitely stop it. In this rare scenario #2 you have to have been backdoored for them to be able to persist.
I expect that over time only more and more people will be trying to do this / there will be more bots out there automatically attacking miners that are reachable from the internet. This is why I disclosed these vulnerabilities to Goldshell (they actually sent me a free SC Box as a reward, and I didn’t ask, that was out of their pure kindness) as they weren’t incredibly difficult to find and over time more people will find them (some have already).
Best of luck and definitely let us know how it turns out!
Let me solve this situation and I will update soon, Thanks.
Hey Annop,
Sounds good! The reason I said you may have to do all of them is that it only takes one of them to change all the other one’s pools for a bot. Basically if it’s in one of them then it will try to change anything it can reach if that makes sense.
This used to be a really big problem on AntMiners years ago as well but they’ve been pretty locked down for a long time. It’s definitely possible to backdoor AntMiners with old firmware though or even other miners such as InnoSilicon (another company I reported vulnerabilities to but they never responded).
It can be pretty hard to detect and track them down once they’ve been backdoored but the SD card wipe is the way to “clean” them. One thing you can do is put your miners on a network that has “isolation mode” on.
On my personal network for example I set up all my miners on 192.168.7.X and have firewall rules that don’t allow them to talk to any other devices on my network. I set it up so I can still talk to them (it lets me dial in) but the miners can’t dial out (except to the internet, just not to my home devices) or dial each other.
Something like this may be good for both damage control as well as prevention since when you do this then an infected miner can’t spread or change the pools on other miners. It’s also preventative security against exploits that haven’t even been discovered yet such as threats potentially from the cloud or the company themselves if their cloud/firmware servers got hacked or an employee went rogue (all situations that can and do happen).
I will eagerly wait to see how it turns out for sure!
Good news!!!
Everything back to normal. I have done all of your mention above, Goldshell should give you more xxx-Box Miner as a reward.
Thank you to Mr.James A. Chambers, You safe my time.
Hey Annop,
Congratulations, that is great work! It feels very good to clean up attacks like this and finally get the upper hand after so much frustration. I’m very glad I could help. Feel free to stop by any time!